Immutable backups are exactly what they sound like: backups that, once written, cannot be changed or deleted. Think of them as a time capsule for your data. This simple but powerful concept makes them your ultimate safety net against ransomware and catastrophic data loss.
They operate on a Write-Once, Read-Many (WORM) principle. Once the data is saved, it's locked in place for a set period. This guarantees you have a clean, untouchable copy to restore from, even if an attacker manages to compromise your primary admin credentials.
Your Last Line of Defense in a Zero-Trust World
The integrity of your backup system is everything. For years, IT professionals and sysadmins treated backup copies as the final word in data safety. But the threat landscape has evolved. Cybercriminals now understand that backup repositories are ground zero in 96% of ransomware incidents. They know if they can neutralize your backups first, you have no choice but to pay.
This strategic shift makes traditional, modifiable backups a massive liability. A backup that a compromised account can delete isn't a recovery tool; it's just another point of failure. This is precisely why immutability isn't just a feature anymore—it's a core requirement for enterprise-level resilience.
The Financial Ledger Analogy
To grasp the concept, think of an immutable backup like a bank's financial ledger. Once a transaction is logged, it's permanent. You can add new entries, but you cannot go back and erase or alter previous ones. This creates a chain of trust that is always reliable.
Immutable backups bring that same unshakeable logic to your data protection strategy:
- Unalterable Copies: Every backup version is sealed in a WORM state. It cannot be encrypted, modified, or prematurely deleted.
- Guaranteed Integrity: The data you recover is byte-for-byte identical to the data you backed up. No tampering, no corruption.
- A Surefire Recovery Path: Even if your entire production environment is compromised—including privileged admin accounts—your immutable copies are safe and sound, waiting to be restored.
This model completely flips the script on the modern ransomware playbook. Instead of discovering your safety net has been destroyed, you have a guaranteed clean recovery point ready to deploy.
"Immutable backups are more than a core cybersecurity function—they are essential to protecting high-stakes data. Immutability isn’t simply a technical feature; it is a foundational safeguard for operational resilience and the integrity of vital systems."
Embracing a Zero-Trust Mentality
The Zero Trust philosophy operates on a simple principle: trust nothing, verify everything. It assumes no user or system is safe, whether it's inside or outside your network perimeter. Immutable backups are the perfect embodiment of this mindset applied to your data.
They don't trust that your admin credentials won't be compromised. They don't trust that your internal network is secure. Instead, they build a technological wall that makes malicious or accidental changes impossible.
By creating an unchangeable, authoritative record of your data, immutable backup solutions give you that one last, definitive line of defense. They ensure that no matter what an attacker throws at you, you always have a path back to business as usual. That's what makes them an absolutely critical component of any modern disaster recovery plan.
How Immutable Backup Technologies Actually Work
To understand why immutable backup solutions are a game-changer for IT infrastructure, you have to look under the hood at the technology that makes data unchangeable. This isn't about setting a "read-only" flag. True immutability is enforced at the storage protocol level, creating a digital fortress around your data that even an administrator with the highest privileges cannot breach.
The entire concept is built on the WORM (Write Once, Read Many) principle. Think of it like carving a message into a stone tablet. Once it's etched, you can't erase it or alter a character. WORM storage applies the same logic to digital files; once a backup is written, the storage system itself blocks any API calls attempting to modify or delete it for a predefined retention period.
This infographic breaks down how these core ideas come together to deliver data protection that is unalterable, permanent, and always recoverable.
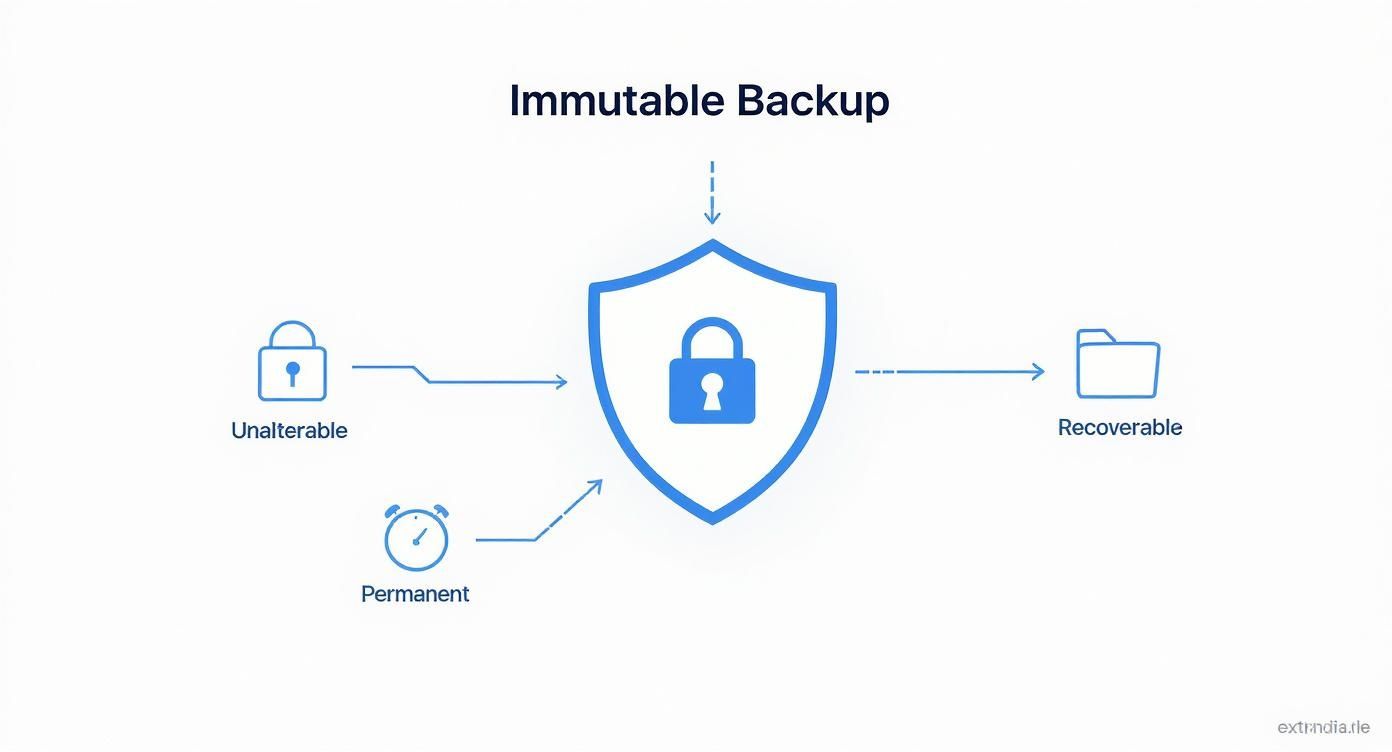
As you can see, it's the trifecta of these three attributes that forms the foundation of a truly cyber-resilient strategy. Your data is safe, it's there for as long as you need it, and you can always get it back.
Object Lock The Cloud Standard for Immutability
In modern cloud and on-premise object storage, the primary mechanism for enabling WORM capabilities is Object Lock. It was first popularized by Amazon S3 and has since become the de facto standard for S3-compatible platforms. It allows you to apply retention policies directly to data objects, making them tamper-proof at the API level.
Object Lock offers two distinct modes, each designed for a specific level of protection:
- Governance Mode: Think of this as a strong safety rail. It prevents most users from overwriting or deleting objects but allows specific users with special IAM permissions (
s3:BypassGovernanceRetention) to alter the retention settings if necessary. It's ideal for preventing accidental deletions while allowing trusted administrators to manage the storage lifecycle. - Compliance Mode: This is the Fort Knox of data protection. Once an object is locked in Compliance Mode, no one can alter or delete it—not even the root account administrator. The data is immutable until the retention period expires. This is the highest level of protection and is often a requirement for meeting strict regulatory compliance mandates like HIPAA, FINRA, or SEC Rule 17a-4.
Here’s the critical takeaway: Compliance Mode effectively creates a logical air gap. Even if a cybercriminal compromises the highest-level admin credentials, they are technologically blocked by the storage API from encrypting or deleting your backups.
Contrasting Hardware and Software Approaches
Immutability can be achieved through either hardware or software-defined methods. Understanding the distinction is key to selecting the right architecture for your environment.
- Hardware-Based Immutability: This approach uses specialized storage appliances with WORM functionality built into the device's firmware. These systems offer extremely robust physical protection but tend to be less flexible and often come with a significant capital expenditure.
- Software-Defined Immutability: This method leverages software policies, like S3 Object Lock, on commodity hardware or in the cloud. It is far more flexible, scalable, and generally more cost-effective, which is why it has become the standard for modern IT environments, including those virtualized with Proxmox VE. To learn more, you can read about how immutable storage works in different environments.
Recent data paints a grim picture: 96% of ransomware attacks now specifically target backup repositories. Attackers know that if they can destroy your only means of recovery, your organization is far more likely to pay the ransom. This is precisely the threat that immutable backups are designed to neutralize.
By ensuring your backup data cannot be altered, you neutralize the attacker's primary leverage. Whether you choose a hardware or software-defined solution, the goal is the same: create a fail-safe copy of your data that can withstand attacks, corruption, and human error.
Choosing the Right Immutable Backup Solution
Selecting the right immutable backup solution is a critical decision that directly impacts your ability to recover from a disaster. With the market for these solutions projected to hit $18.7 billion by 2033, the options can feel overwhelming. This growth reflects a fundamental shift in data protection strategy: immutability is no longer a "nice-to-have" feature—it's the bedrock of modern cyber resilience.
To make an informed choice, you must look beyond marketing claims and analyze the technical capabilities. A solution for a small business won't scale for a complex enterprise, so start with a clear assessment of your infrastructure, RTO/RPO targets, and compliance requirements.
Essential Features to Scrutinize
Not all immutable backup platforms are created equal. As you evaluate vendors, prioritize solutions that offer a robust feature set designed for enterprise-level security and management.
Here’s what should be on your technical checklist:
- Granular Retention Policy Enforcement: The platform must allow you to set and enforce retention periods that cannot be overridden by standard administrative accounts. Look for explicit support for both S3 Object Lock Governance and Compliance modes to balance operational flexibility with absolute data integrity.
- Cryptographic Verification: This is non-negotiable. A top-tier solution will use cryptographic hashing (like SHA-256) and checksums to verify the integrity of each backup chunk. This proves that the data being restored is a bit-for-bit, untampered copy of the original—a critical requirement for regulated industries.
- Role-Based Access Control (RBAC): Immutability protects the data, but strong RBAC protects the configuration. The system must provide fine-grained control over who can create, manage, or view backup jobs and datastores. This mitigates risks from insider threats or compromised accounts.
- Seamless Platform Integration: The solution must integrate seamlessly with your existing technology stack. Whether you run Proxmox VE, VMware, or use tools like Veeam or Proxmox Backup Server, native integration is key to avoiding operational friction and complex scripting. To see how different platforms approach this, it's worth reviewing some of the top backup solutions for small businesses.
On-Premises vs. Cloud vs. Hybrid Deployments
The deployment model for your immutable repository is another critical factor, affecting cost, performance, and security posture. Each approach has distinct trade-offs, and the optimal choice depends on your organization's specific needs.
To help you evaluate the options, here is a technical breakdown of the different deployment models.
Comparison of Immutable Backup Deployment Models
This table compares the key characteristics of on-premises, cloud-based, and hybrid immutable backup solutions to help IT leaders choose the best fit for their organization's needs.
| Attribute | On-Premises Solution | Cloud-Based Solution (e.g., S3 Object Lock) | Hybrid Solution |
|---|---|---|---|
| Performance | Highest performance. Low-latency local network access provides the fastest backup and restore times. | Performance is constrained by internet bandwidth. Latency can be a significant factor for large-scale restores. | Balanced performance. Provides fast local restores for recent data while leveraging offsite cloud storage for long-term archives. |
| Cost | High upfront capital expense (CapEx) for hardware, but predictable ongoing operational costs (OpEx). | Near-zero CapEx. A pay-as-you-go OpEx model, but costs can become unpredictable due to egress fees and data growth. | A mix of CapEx for local hardware and variable OpEx for cloud storage, offering a predictable cost model with cloud scalability. |
| Security | Full control over physical and network security, but the responsibility is 100% on your internal team. | A shared responsibility model. The provider secures the underlying infrastructure, but you are responsible for data and access configuration. | Offers layered security, combining the physical control of on-prem with the robust security features of a major cloud provider. |
| Scalability | Scaling requires procuring and provisioning new hardware, which can be slow and expensive. | Virtually infinite scalability on demand. You can expand storage capacity instantly via API calls. | Highly scalable. The cloud tier handles data growth without requiring immediate on-prem hardware expansion. |
As you can see, each model has its place. The decision comes down to balancing performance, budget, and control against your specific operational requirements.
A hybrid model often provides the best of both worlds. It aligns perfectly with the 3-2-1-1-0 backup rule by maintaining a fast local copy and an immutable offsite copy for ultimate disaster recovery.
Aligning the Solution with Business Goals
Finally, your choice must align with business objectives. Before committing to a solution, define your Recovery Point Objectives (RPO) and Recovery Time Objectives (RTO). How much data can you afford to lose, and how quickly must services be restored? These metrics will dictate the required architecture. For organizations with managed infrastructure, our Proxmox Backup as a Service is built to meet aggressive RTO/RPO targets with immutability at its core.
Don't forget regulatory compliance. Whether you're governed by HIPAA, GDPR, or another framework, ensure any solution you consider can meet those stringent requirements. By asking the right technical questions and matching the technology to your business needs, you can select an immutable backup solution that truly protects your organization.
Implementing Immutable Backups Step by Step
Let's translate theory into practice. This section provides a technical walkthrough for configuring a robust, immutable backup system for a Proxmox VE environment. We will connect Proxmox Backup Server (PBS) to an S3-compatible object storage service with Object Lock enabled.
Following these steps will transform your standard backup routine into a fortress against ransomware, creating an unchangeable, offsite copy of your critical VM and container data.

Step 1: Create and Secure Your S3 Bucket
The foundation of this architecture is an S3 bucket configured with Object Lock. This step must be performed correctly from the outset.
Important: Object Lock can only be enabled during bucket creation. You cannot enable it on an existing bucket. If you miss this step, you must create a new bucket.
- Log into your S3-compatible storage provider's console (e.g., AWS, Wasabi, Backblaze B2).
- Create a new bucket. Choose a globally unique and descriptive name.
- Enable Object Lock. During the creation process, locate and enable the "Object Lock" setting. This is the critical step that enables immutability.
- Create a dedicated IAM user. Adhering to the principle of least privilege, create a new IAM user with programmatic access. Attach a policy that grants it only the permissions necessary for PBS to operate (
s3:PutObject,s3:GetObject,s3:ListBucket, etc.) on that specific bucket. Do not use root credentials. - Securely store the access key and secret key. These credentials will be used to connect PBS to the bucket. Store them securely in a password manager or secrets management system.
Step 2: Configure the Datastore in Proxmox Backup Server
With the S3 bucket prepared, add it as a remote datastore in your Proxmox Backup Server instance. This tells PBS where to send backup data for immutable, long-term storage. This can be done via the web UI or the command line.
Using the Command Line (CLI):
For automation and precision, the CLI is the preferred method for sysadmins.
# Example using proxmox-backup-manager to add an S3 remote datastore
proxmox-backup-manager remote create s3-immutable-backups
--endpoint your-s3-endpoint.com
--bucket your-bucket-name
--access-key-id YOUR_ACCESS_KEY
--secret-access-key YOUR_SECRET_KEY
Using the Web GUI:
- Navigate to Datastores in the PBS menu and click Add.
- Select Object Storage / S3.
- Fill in the required fields:
- Datastore Name: A descriptive name like
s3-immutable-backups. - S3 Endpoint: The URL provided by your storage vendor.
- Bucket Name: The exact name of the bucket created in Step 1.
- Access Key ID & Secret Access Key: The credentials generated for the dedicated IAM user.
- Datastore Name: A descriptive name like
- Click Add. PBS will perform a connection test to validate the credentials and bucket access.
Step 3: Set Up Your Backup Jobs and Retention Policies
Now, configure a sync job in PBS to transfer data from a local datastore to your newly created S3 immutable datastore. The retention settings you define are critical—they determine how long your backups are protected from deletion by Object Lock.
A best practice is to follow the 3-2-1-1-0 rule:
- 3 copies of your data.
- 2 different media types.
- 1 copy stored offsite.
- 1 copy that is immutable or air-gapped.
- 0 errors after recovery verification.
Our architecture achieves this: the first copy is on your local Proxmox storage, the second is on the local PBS datastore (for fast restores), and the third is the offsite, immutable copy in the S3 bucket.
- In the PBS web interface, navigate to your local datastore, select Sync Jobs, and click Add.
- Configure the sync job:
- Remote: Select the
s3-immutable-backupsremote you just created. - Remote Datastore: Specify a name for the datastore on the remote S3 target.
- Schedule: Define how often the sync should run (e.g., daily).
- Remote: Select the
- Configure retention policies in PBS for that S3 datastore. For example, setting
keep-daily=14tells PBS to retain the last 14 daily backups. Once these backups are synced to the S3 bucket with Object Lock, they cannot be deleted for 14 days, even if an administrator attempts to delete them from PBS or the S3 console.
Step 4: Verify Immutability
Trust, but verify. The final and most critical step is to confirm that the immutability lock is working as expected.
The most effective way to do this is by attempting to manually delete a backup chunk directly from the S3 bucket.
- Log into your S3 provider's console and navigate to the bucket.
- Browse to the
.chunksdirectory and locate any data chunk file. - Attempt to delete the file.
You should receive an "Access Denied" error or a similar message explicitly stating the object is protected by a retention policy. This failed deletion attempt is your confirmation of success. It proves that your immutable backup solution is correctly configured and your data is safe from both malicious and accidental deletion.
Integrating Immutability into Your Disaster Recovery Plan
An immutable backup is a powerful tool, but its true value is realized only when it is fully integrated and validated within your organization's disaster recovery (DR) plan. An untested backup, even an immutable one, is merely a theoretical asset. A properly integrated and regularly tested immutable backup is your guaranteed path to operational continuity.
This integration shifts your DR strategy from reactive hope to proactive certainty. You can operate with the confidence that a clean, verifiable copy of your data is always available. It’s the difference between having a fire extinguisher on the wall and having a trained fire response team that drills monthly.

Regularly Testing and Validating Your Backups
The most common point of failure in DR is a lack of rigorous, regular testing. Many organizations invest in immutable backup solutions but never perform a test restore. When disaster strikes, they discover a critical flaw in their process at the worst possible moment.
Regular validation is non-negotiable. Here’s what a professional testing regimen looks like:
- Automated Integrity Checks: Configure Proxmox Backup Server to run routine
verifyjobs. These jobs read back and check the checksums of backup data without performing a full restore, identifying potential bit rot or corruption early. - Scheduled Test Restores: On at least a quarterly basis, perform a full restore of a non-critical system (e.g., a development web server or a staging database) into an isolated network sandbox. This validates both data recoverability and your team's familiarity with the restore procedure.
- Full DR Simulation: Annually, conduct a full-scale DR drill. This exercise should simulate a complete production outage and involve restoring multiple interdependent systems (e.g., domain controllers, application servers, and databases) from the immutable repository to prove you can meet your Recovery Time Objectives (RTOs) under pressure.
Simulating a Full Ransomware Recovery
Let's walk through a real-world recovery workflow for a KVM-based virtual server following a ransomware attack, using data from your S3 immutable repository.
- Isolate the Infected Environment: The moment an attack is confirmed, sever all network connections to compromised systems using firewall rules or VLAN changes. This contains the threat and prevents lateral movement.
- Identify the Last Known Good Backup: Review backup logs to pinpoint the most recent backup snapshot created before the time of infection. This is your designated recovery point.
- Initiate the Restore from the Immutable Repository: Using the Proxmox Backup Server interface, initiate a restore job for the target VM. Ensure you select the clean, immutable S3 datastore as the source.
- Restore to an Isolated "Clean Room" Network: Crucially, do not restore the VM directly back into the production environment. Instead, restore it to a quarantined network segment with no ingress or egress traffic allowed.
- Scan and Validate the Restored VM: Once the VM is running in the clean room, perform comprehensive malware and vulnerability scans. This step verifies that no dormant malicious code was present within the backup itself.
- Promote to Production: Only after confirming the restored machine is 100% clean can you safely migrate it back into the production network.
This structured workflow ensures a methodical and secure recovery. The immutable nature of the backup guarantees the source data is untampered, allowing your team to focus on validating system integrity before reintroducing it to the network.
Managing Storage and Retention Costs
A key operational challenge with immutable backups is storage management. Since data cannot be deleted until its retention period expires, costs can escalate without careful planning. A smart, tiered retention strategy is essential for balancing security and cost-effectiveness. Our guide on the backup and restore process provides deeper insights into building these strategies.
Consider implementing a tiered retention policy:
- Short-Term (Hot Storage): Keep daily backups for 14-30 days in your primary immutable repository for rapid recovery from recent incidents.
- Medium-Term (Warm Storage): Retain weekly backups for 90 days.
- Long-Term (Cold Storage): Archive monthly backups for 1-7 years to meet compliance and legal requirements, leveraging lower-cost S3 storage tiers like Glacier Deep Archive.
This tiered approach ensures you have recent backups immediately accessible while optimizing the costs of long-term, immutable data. Ultimately, immutable backups become a cornerstone of your overall data recovery and IT emergency solutions, providing the reliable lifeline you need when a critical incident occurs.
The Urgent Business Case for Immutable Backups
Migrating to an immutable backup architecture is not just an IT project; it is a critical business decision with significant financial implications. While it is well-understood that traditional backups are a primary target for attackers, a dangerous gap often exists between acknowledging this risk and implementing a solution. The threat landscape evolves daily, yet many organizations continue to operate on outdated assumptions about data protection.
This is not theoretical. The latest industry data paints a stark picture: 96% of ransomware attacks now specifically target backup systems. Despite this, only 28% of IT professionals currently utilize immutable backup solutions. This discrepancy leaves the vast majority of businesses critically exposed to catastrophic data loss and operational paralysis. You can review the statistics in the latest data protection trends report.
From Technical Feature to Business Survival
Adopting immutable backups is not about adding a single feature—it's about reinforcing the three core pillars of corporate resilience. It is an investment in business continuity that provides a clear ROI the moment an incident is averted.
This strategic shift delivers tangible results:
- Rock-Solid Cyber Resilience: Immutability provides a guaranteed clean, unchangeable recovery point, neutralizing ransomware's primary leverage. Your recovery plan transitions from a hopeful strategy to a reliable, repeatable, and auditable process.
- Simplified Regulatory Compliance: For businesses governed by frameworks like HIPAA, GDPR, or PCI-DSS, immutable backups offer a verifiable, tamper-proof audit trail for data retention and integrity. This simplifies compliance audits and helps avoid severe financial penalties associated with data mismanagement.
- A Guaranteed Path to Recovery: By eliminating the risk of backup deletion or encryption, immutability ensures you can always restore operations. This is your primary defense against the devastating financial and reputational damage of a successful cyberattack.
The question is no longer whether your organization can afford to implement immutability, but whether it can afford not to. Inaction is a direct acceptance of unacceptable risk.
It's time to conduct a thorough risk assessment of your current backup strategy against modern threats. An investment in immutable architecture is not an expense—it is a foundational component of your organization's survival.
Questions We Hear All the Time About Immutable Backups
When evaluating immutable backup solutions, several key technical questions consistently arise. Addressing these is crucial for designing a data protection strategy that is both secure and operationally sound. Here, we tackle the most common questions from IT professionals and system administrators.
This section provides the practical, authoritative answers needed to move forward with a backup plan that works in the real world.
How Is This Different from Air-Gapped Backups?
This is a fundamental question. Both are powerful strategies for ransomware defense, but they are architecturally distinct.
An air-gapped backup is a copy of data that is physically or logically disconnected from the network. Classic examples include offline tapes stored in a vault or a rotated external hard drive. The physical isolation offers exceptional security, but restoration is often a slow, manual process requiring physical access, which can significantly extend RTO.
Immutable backups, conversely, are typically online and accessible. They use software-defined policies like S3 Object Lock to enforce a WORM state. This digital lock prevents modification or deletion at the API level, offering an optimal balance of high-level security and rapid, low-latency data access for restores.
Think of it this way: an air-gapped backup is like storing gold bars in a vault. It is incredibly secure but difficult to access quickly. An immutable backup is like a bank's blockchain-based ledger—it's online and accessible, but once an entry is recorded, it cannot be altered by anyone.
Won't This Get Expensive with Storage Costs?
This is a valid operational concern. Since immutable data cannot be deleted until its retention period expires, you cannot manually "clean up" old backups to reclaim space. This makes capacity planning and data lifecycle management essential.
However, modern object storage platforms and backup software are designed to mitigate these costs:
- Storage Tiering: Automated lifecycle policies can transparently move older, immutable data to lower-cost archival tiers (e.g., Amazon S3 Glacier Instant Retrieval or Deep Archive).
- Deduplication and Compression: Advanced backup software like Proxmox Backup Server performs client-side deduplication and compression before data is written to the immutable repository, drastically reducing the storage footprint and associated costs.
When these technologies are properly implemented, the cost of immutable backup solutions becomes a manageable and predictable operational expense—a sound investment in business survivability.
Can't a Privileged Admin Just Delete Everything?
This question addresses the core value proposition of immutability. If the system is correctly configured using a feature like S3 Object Lock in Compliance Mode, the answer is an unequivocal no.
No user can delete the backups. This includes a cloud provider root user, a domain administrator, or the engineer who configured the system.
The retention lock is enforced at the storage system's API layer, making deletion a technological impossibility until the retention period expires. This provides the ultimate safeguard against both external attackers with compromised credentials and the risk of a malicious insider.
At ARPHost, LLC, we don’t just offer backups; we build a fortress for your data. Our Proxmox Backup as a Service is engineered with immutable storage at its core, giving you a final, unbreakable line of defense. Protect your critical infrastructure with a solution built for the threats of today.



[…] that syncs data at least every 15 minutes, such as ZFS replication snapshots. Technologies like immutable backup solutions are essential for meeting tight RPOs while also protecting against […]
[…] plan. For robust protection against accidental deletion or corruption, you can learn more about immutable backup solutions to further secure your critical […]
[…] and ransomware, it's worth understanding different backup strategies. You can learn more about immutable backup solutions for ransomware defense as a powerful added security […]
[…] cloud. This underscores the importance of a robust data protection strategy, such as implementing immutable backup solutions to safeguard critical data regardless of its […]
[…] A robust security posture requires both strong defenses and a solid recovery plan. This intersection is detailed in our guide on immutable backup solutions. […]