Co-located hosting is a data center service where an organization rents physical space, power, and cooling for its privately owned server and networking hardware. Instead of building and managing an on-premises data center, you deploy your bare metal servers, switches, and firewalls within a specialized, third-party facility.
Think of it as owning high-performance computing hardware and leasing a secure, enterprise-grade environment to house it. You retain full ownership and root-level control over your infrastructure stack, while the colocation provider manages the complex and capital-intensive facility infrastructure, redundant power, industrial cooling, multi-layered physical security, and high-speed network connectivity.
Understanding the Colocation Model
Co-located hosting occupies a critical middle ground between the significant capital expenditure (CapEx) of a private data center and the potential limitations of Infrastructure-as-a-Service (IaaS) cloud models. You supply the hardware stack you trust, from your Proxmox VE cluster to your Juniper firewalls—and the provider delivers the resilient environment required to keep it online. This includes the building, redundant power grids (UPS, generators), precision HVAC systems, and carrier-neutral network access.
This model is ideal for organizations requiring absolute control over their hardware and software configurations but seeking to offload the immense operational burden of facility management. You maintain full ownership and administrative access to your equipment while leveraging an enterprise-grade infrastructure that is often cost-prohibitive to build and maintain in-house.
Who Benefits from Co-Located Hosting
While not a universal solution, colocation provides a precise balance of control, cost-efficiency, and performance for specific technical use cases.
- High-Performance Computing (HPC): For workloads like data analytics, AI/ML model training, or scientific simulations, colocation enables the deployment of custom-configured bare metal servers in an environment engineered for high power density and efficient cooling.
- Robust Disaster Recovery (DR) Sites: A geographically distinct colocation facility is a cornerstone of a sound business continuity strategy. It provides a highly resilient site for housing replication targets and backup infrastructure, ensuring operational continuity in the event of a primary site failure.
- Seamless Hybrid Cloud Integration: Modern data centers offer “cloud on-ramps”—direct, private, low-latency connections to hyperscale cloud providers (e.g., AWS Direct Connect, Azure ExpressRoute). This allows you to host sensitive databases or legacy applications on private hardware while connecting them to scalable cloud services.
- Compliance and Data Sovereignty: For regulated industries like healthcare (HIPAA) or finance (PCI DSS), colocation provides physical control over data within a certified, auditable facility, satisfying critical data residency and security requirements.
In short, co-located hosting is for the IT manager, sysadmin, or solutions architect who requires granular infrastructure control, verifiable security, and predictable operational expenditure. It is a scalable solution that doesn’t require expertise in data center engineering.
The Growing Demand for Colocation
Market data validates the model’s relevance. The global data center colocation market is projected to grow from USD 104.2 billion in 2025 to USD 204.4 billion by 2030. This growth is driven by the expansion of AI, HPC, and the strategic imperative for flexible hybrid cloud architectures. You can explore more data on colocation market trends to see what’s driving this shift.
To understand how this model fits within a broader strategy, our technical comparison of private cloud vs. public cloud offers critical context.
The Strategic Benefits of Colocation
Opting for co-located hosting is a strategic infrastructure decision that yields tangible technical and financial advantages over maintaining an on-premises data center. The primary benefit is achieving enterprise-grade reliability without the prohibitive CapEx of building a comparable facility.
This approach allows you to bypass the costs associated with construction, redundant power infrastructure, industrial HVAC systems, and multi-layered physical security. That CapEx is converted into a predictable operational expense (OpEx), enabling your technical teams to focus on server and application management rather than facility operations.
This diagram illustrates how colocation balances infrastructure ownership, provider services, and hybrid cloud connectivity.
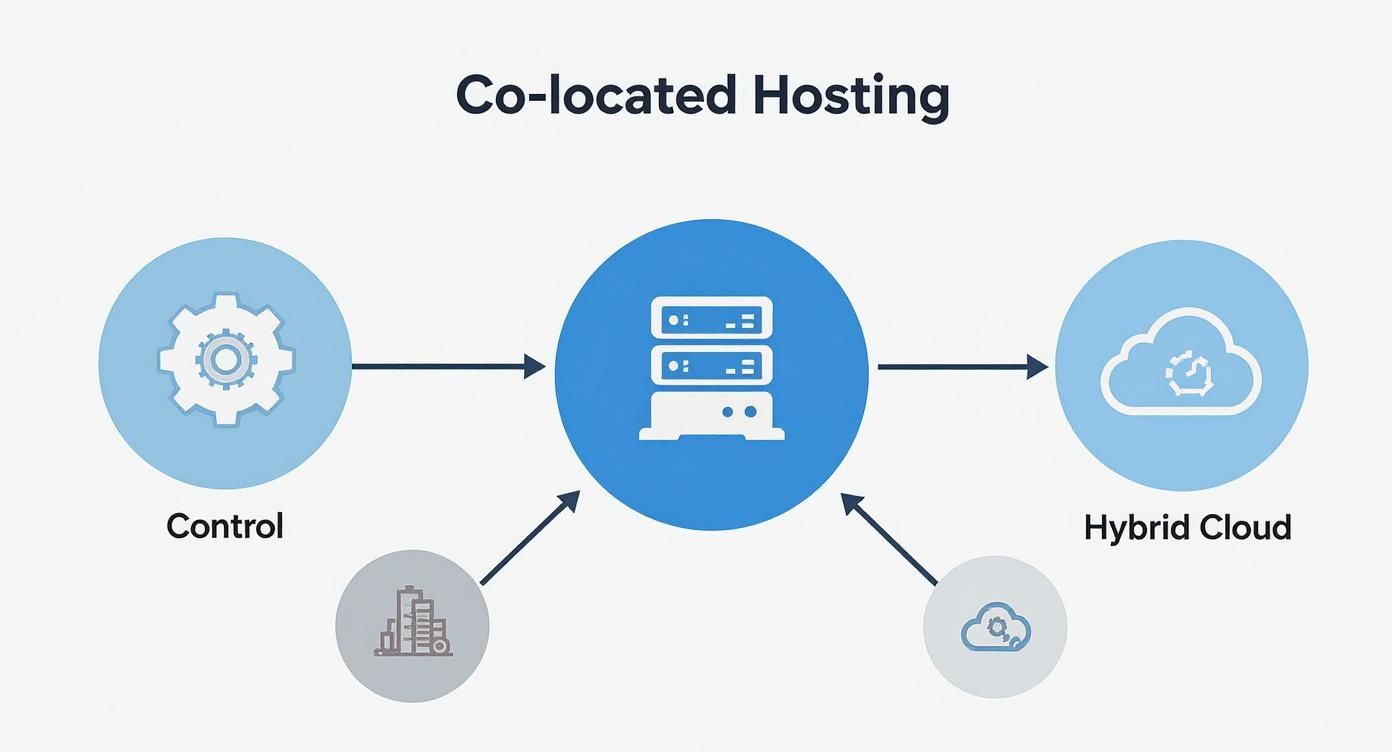
As shown, you retain direct control over your server, storage, and networking hardware while leveraging the provider’s resilient infrastructure and direct access to hybrid cloud services.
Uptime and Performance Guarantees
A key technical driver for colocation is access to stringent Service Level Agreements (SLAs). A reputable provider guarantees power and network uptime, often at 99.999% availability, a resiliency target that is exceedingly complex and expensive to achieve with an on-premises setup. This is backed by multiple utility feeds, enterprise-grade UPS systems, and diesel backup generators.
Furthermore, colocation facilities serve as major connectivity hubs. They provide a carrier-neutral environment with access to a diverse ecosystem of network providers. This allows you to engineer a resilient, multi-homed network architecture that can survive a specific carrier outage and optimize for cost and performance.
By migrating to a data center, you are effectively transferring the risk of infrastructure downtime. The provider’s business model is predicated on resiliency, ensuring your hardware remains powered, cooled, and connected—all contractually guaranteed.
Enabling Powerful Hybrid Cloud Environments
Modern colocation is a foundational component of any effective hybrid cloud strategy. Premier data centers offer “cloud on-ramps,” which are dedicated, private, low-latency network connections to public cloud providers like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud.
These private interconnects bypass the public internet, delivering key technical advantages:
- Reduced Latency: Private connections significantly lower round-trip time (RTT) between your physical servers (e.g., a Proxmox cluster) and cloud services, which is critical for applications requiring real-time data synchronization.
- Enhanced Security: Data in transit is isolated from the public internet, mitigating exposure to common network-based threats.
- Predictable Performance: By avoiding public internet congestion, you achieve consistent and reliable network throughput for hybrid workloads.
This architecture enables you to run high-I/O databases or legacy applications on dedicated bare metal servers while seamlessly connecting them to scalable cloud services. It is the ideal foundation for maximizing hardware utilization. Understanding the advantages of virtualizing servers within this model is key to consolidating workloads and optimizing resource allocation in your secure rack.
This fusion of physical control and cloud agility provides a powerful, future-proof infrastructure platform.
Choosing Between Managed and Unmanaged Colocation
After deciding on colocation, the next critical decision is the service model: managed or unmanaged. The choice depends entirely on your internal IT capabilities, resources, and strategic focus.
Unmanaged colocation is the traditional DIY model. The provider delivers the secure rack space, conditioned power, cooling, and network drop. Responsibility for everything else, from hardware installation to OS patching, falls to you.
The Unmanaged DIY Approach
With unmanaged colocation, your IT team assumes full responsibility for the entire infrastructure lifecycle. This includes physically racking servers, cabling equipment, installing and hardening operating systems like Proxmox VE, and performing all ongoing maintenance. When a drive fails in a ZFS pool at 3 AM or a zero-day vulnerability requires immediate patching, your team is responsible for the response.
This model offers maximum control, making it a preferred choice for organizations with deep in-house expertise and specific configuration or compliance mandates.
- Initial Setup: You are responsible for the physical installation of servers, switches (e.g., Juniper EX series), and firewalls in the cabinet.
- Software Provisioning: Your team deploys, configures, and hardens the hypervisor, operating systems, and application software.
- Ongoing Maintenance: All OS and software patching, firmware updates, and hardware replacements are your responsibility.
- Monitoring: You must implement and manage your own monitoring solutions (e.g., Zabbix, Prometheus) to track infrastructure health and performance.
The Managed Services Advantage
Managed colocation extends the provider’s role from facility operator to an extension of your IT team. The provider’s experts handle the day-to-day operational tasks, freeing your internal resources to focus on strategic initiatives and application development.
This service transcends basic “remote hands” for reboots. A true managed service provider offers proactive monitoring, OS patch management, firewall policy administration on devices like Juniper SRX firewalls, and backup and disaster recovery management. For organizations that require enterprise-level expertise without the associated headcount, our guide on managed IT services for small business details this collaborative model.
Managed colocation bridges the gap between raw infrastructure and a fully supported, production-ready environment. It is designed for organizations that demand the control of dedicated hardware but recognize the strategic value of outsourcing its maintenance and security to specialized experts.
This approach is highly effective for organizations where developer or engineer time is better allocated to core business logic than to diagnosing a faulty RAM module.
The demand for expert support is a significant driver of market growth. The U.S. colocation market is expected to reach USD 23.7 billion by 2025, with a projected CAGR of 14.9% through 2030, largely driven by businesses seeking flexible contracts and expert managed services to facilitate scalable growth. Discover more insights about the U.S. colocation market to understand the factors behind this expansion.
The optimal choice depends on your team’s skillset, budget, and strategic priorities, requiring a careful balance between the need for absolute control and the operational efficiency gained from a managed partnership.
How to Accurately Budget for Colocation Costs
A successful co located hosting deployment depends on a precise understanding of its Total Cost of Ownership (TCO), not just the recurring monthly invoice. While core fees for space and power are predictable, variable and one-time costs can significantly impact your budget if not accounted for upfront. A detailed financial model is essential to prevent unexpected expenditures.
Your forecast must begin with the primary recurring costs, which form the foundation of your colocation budget.

Core Recurring Costs
Your monthly operational expenditure (OpEx) will primarily consist of three components: space, power, and network bandwidth. Each is metered and billed differently, requiring careful estimation based on your specific hardware and performance requirements.
- Rack Space: This is the physical footprint your hardware occupies, typically sold by the rack unit (‘U’, standardized at 1.75 inches of vertical space) or by the cabinet (e.g., quarter, half, or full 42U rack).
- Power: Providers typically offer two models. Committed Information Rate (CIR) provides a fixed power allocation (e.g., a 20A/120V circuit) for a flat monthly fee, regardless of usage. Metered power bills based on actual kilowatt-hour (kWh) consumption, offering flexibility but less budget predictability.
- Bandwidth: This is your data transit to the internet. Common billing models include metered (per-gigabyte pricing), unmetered (a flat rate for a fixed port speed, like 1 Gbps), or the 95th percentile method, which bills based on sustained usage while ignoring brief traffic bursts.
Uncovering Hidden and One-Time Expenses
Beyond core monthly fees, several other costs can arise, either as one-time charges or on an as-needed basis. These “hidden” expenses often surprise teams without deep colocation experience.
Your colocation TCO is like an iceberg. The monthly invoice for space and power is the visible tip. One-time setup fees, remote hands charges, and recurring cross-connect costs are the substantial expenses below the surface.
Failing to account for these items will lead to significant budget overruns. Ensure they are factored into both your initial and ongoing financial models.
Actionable Budgeting Example
Let’s develop a TCO estimate for a small bare-metal server deployment to illustrate these concepts with a practical, step-by-step example.
Scenario: Deploy a 3-node Proxmox VE cluster using 2U servers, each with a redundant 750W power supply unit (PSU).
- Rack Space Calculation: Three 2U servers require 6U of vertical space (
3 servers * 2U/server). A quarter rack (typically 10U) provides sufficient space for the servers, a 1U top-of-rack switch (e.g., a Juniper EX2300), and a 1U firewall, with room for future expansion. - Power Draw Estimation: A server’s PSU rating is its maximum potential draw, not its typical operational consumption. A conservative estimate for average utilization is 60%.
- Calculation:
3 servers * 750W * 0.60 = 1350W(or 1.35 kW). This is the sustained power figure you should provide to a prospective data center for an accurate quote.
- Calculation:
- Cross-Connects: A physical fiber or copper connection is required from your cabinet to your chosen network carrier’s point of presence (POP) within the data center. This typically involves a one-time setup fee and a recurring monthly charge. Budget for at least one.
- Remote Hands: Even with a stable environment, it is prudent to budget for a few hours of remote support per quarter for tasks like rebooting a non-responsive server, swapping a failed drive in a ZFS array, or checking physical port status.
- Setup Fees: Most providers charge a non-recurring fee for the initial installation of your space, power circuits, and network port provisioning.
By accurately calculating power needs and building in contingencies for support and connectivity, you can construct a comprehensive budget that reflects the true TCO of your co located hosting environment.
Navigating Security and Compliance in Colocation
In a colocation environment, security is a shared responsibility model, a concept also fundamental to cloud computing. Understanding the clear demarcation between the provider’s responsibilities and your own is critical to designing a secure and compliant infrastructure stack.
The data center provider is responsible for the physical and environmental security of the facility. They act as the guardian of the physical perimeter, creating a hardened shell for your equipment.

Their responsibilities encompass a multi-layered security strategy to govern physical access and ensure operational continuity.
- Robust Physical Security: This includes 24/7/365 on-site security personnel, comprehensive video surveillance (CCTV), and multi-factor access controls, often incorporating biometric scanners and mantraps at all critical entry points.
- Strict Environmental Controls: The provider manages industrial-grade HVAC systems, advanced fire suppression (e.g., VESDA with clean agent systems), and redundant power infrastructure to protect hardware from physical threats.
- Facility-Level Compliance: A reputable provider maintains and provides evidence of key industry certifications, such as SOC 2 Type II, ISO 27001, and attestations for regulatory frameworks like HIPAA or PCI DSS.
The demand for these certified facilities is growing rapidly. The Asia Pacific market, for example, is projected to grow at a CAGR of 19.2% from 2025 to 2030, driven by stringent data sovereignty and security regulations.
Your Role in Securing the Stack
While the provider secures the facility, you are responsible for securing everything within your cabinet. Your responsibilities begin where theirs end, covering the entire technology stack from the physical server hardware up to the application layer.
The provider supplies a secure vault; you are responsible for locking the safe inside it. A failure to secure your own hardware, operating systems, and network configurations will expose critical assets, regardless of the facility’s physical security posture.
This requires taking ownership of several key domains to ensure end-to-end security for your co-located infrastructure.
A Security Checklist for Colocation Tenants
To protect your assets effectively, your security strategy must address your hardware, network, and data. Follow these best practices as a starting point:
- Harden Servers and Operating Systems: Maintain a rigorous patch management schedule for all operating systems and software. A simple
apt update && apt upgrade -yon a Debian/Ubuntu-based system is a start, but should be part of a larger, automated patching strategy. Disable all unnecessary services and ports and enforce strong authentication policies, including multi-factor authentication (MFA) for all administrative access (e.g., SSH key-based authentication). - Configure Network Security Appliances: Deploy and correctly configure your firewalls (e.g., Juniper SRX) to control ingress and egress traffic. Implement strict, least-privilege access control lists (ACLs) and leverage network segmentation with VLANs to isolate critical workloads, such as separating a database server from a web-facing application server.
- Implement Private Networking: Utilize private IP address space (RFC 1918) and a dedicated management VLAN for inter-server communication and administrative access. This keeps sensitive management traffic (e.g., Proxmox cluster communication, SSH) off the public internet, dramatically reducing your attack surface.
- Establish a Disaster Recovery Plan: Physical security addresses only one class of risk. It is essential to plan for component or site failure by developing a robust IT disaster recovery plan. This plan must outline procedures for data backups (e.g., using Proxmox Backup Server), hardware failure scenarios, and failover processes to a secondary site if applicable.
A Step-by-Step Guide to Selecting Your Provider
Selecting the right partner for your co-located hosting is a critical infrastructure decision with long-term implications for performance, reliability, and security. The evaluation process must extend beyond marketing materials to a technical deep-dive into the facility’s core capabilities.
Before engaging with providers, develop a technical requirements checklist. This document serves as a structured framework for a head-to-head comparison, enabling you to ask precise, targeted questions that reveal the operational maturity of a data center.
Evaluating Network Infrastructure
A data center is fundamentally a connectivity hub. Its network architecture should be a primary focus of your evaluation, as it directly impacts application performance and resilience.
- Carrier Diversity: How many unique network carriers have a physical point-of-presence (POP) in the facility? A rich, carrier-neutral ecosystem provides redundancy, competitive pricing, and routing flexibility.
- DDoS Mitigation: Describe your Distributed Denial of Service (DDoS) mitigation capabilities. Is it an inline, always-on service or a reactive, on-demand solution? What are the capacity limits (Gbps, Mpps) of the scrubbing platform?
- Peering Agreements: Do you have direct peering relationships with major Tier 1 networks, IXPs (Internet Exchange Points), and public cloud providers (e.g., AWS, Azure)? Direct peering can significantly reduce latency for hybrid cloud traffic.
- Cross-Connect Process: What is the process, SLA, and cost structure for provisioning a physical cross-connect to a carrier or another tenant? Clarify both non-recurring charges (NRC) and monthly recurring charges (MRC).
Assessing Power and Cooling Systems
Power and cooling infrastructure are the lifeblood of your hardware. Redundancy in these systems is non-negotiable, as a failure in either results in an immediate outage.
Your inquiry should focus on resiliency and efficiency metrics.
- Power Redundancy: What is the power redundancy configuration (e.g., N+1, 2N)? 2N represents the highest standard, featuring two fully independent and mirrored power distribution systems from the utility entrance to the rack PDU. N+1 provides a single additional component for failover.
- PUE Rating: What is the facility’s design and operational Power Usage Effectiveness (PUE)? A PUE rating closer to 1.0 indicates higher energy efficiency, which can translate to lower operational costs.
- Backup Power: What is the fuel capacity of the on-site generators, and how long can the facility run at full load during a utility outage? When was the last full-load failover test conducted for both the UPS and generator systems?
Provider selection is an exercise in risk mitigation. You are not merely renting rack space; you are investing in an operational partner whose infrastructure becomes a direct extension of your own. Their ability to manage power, network, and physical security events is your primary defense against downtime.
Analyzing Support and Service Level Agreements
When a critical system fails, the competence of the provider’s support team and the contractual guarantees in the Service Level Agreement (SLA) are paramount.
- SLA Guarantees: Request the specific SLA metrics for power, network availability, and environmental conditions (temperature/humidity). What are the service credit penalties for failing to meet these guarantees?
- Remote Hands Services: What is the defined scope of your “remote hands” service? Request a detailed menu of tasks (e.g., swapping hot-swap drives, power cycling equipment, checking cable connections, installing a KVM console) and the associated hourly or per-incident rates.
- Data Center Tour Checklist: An on-site tour is essential. Observe operational discipline. Is under-floor cabling managed neatly in trays, or is it a “spaghetti mess”? Are Power Distribution Units (PDUs) and circuits clearly labeled? The physical organization of a facility is often a strong indicator of its operational rigor.
Common Questions About Co-Located Hosting
When evaluating infrastructure strategies, several key technical questions consistently arise. Here are concise answers for IT professionals considering colocation.
Can My Colocated Servers Connect to the Public Cloud?
Yes, and this capability is a primary driver for modern co-located hosting. Direct connectivity between your private hardware and public clouds like AWS, Azure, and Google Cloud is a core tenet of hybrid cloud architecture.
This is achieved via “cloud on-ramps”—dedicated, private network connections (e.g., AWS Direct Connect, Azure ExpressRoute) that bypass the public internet. The result is a secure, low-latency, high-throughput link, enabling you to run I/O-intensive databases or legacy applications on bare metal while leveraging scalable cloud services for analytics, development, or object storage.
What Is the Difference Between a U and a Rack?
These terms define the physical space leased within a data center.
- A ‘U’ is the standard unit of measurement for the vertical height of rack-mountable equipment. 1U is standardized at 1.75 inches. Most enterprise servers are 1U or 2U in height.
- A ‘rack’ (or cabinet) is the physical steel enclosure that houses the equipment. A standard full rack provides 42U of vertical space, but providers also offer partial products like a half-rack (~21U) or a quarter-rack (~10U).
Who Replaces Failed Hardware in a Colocation Setup?
In a standard colocation agreement, you are responsible for all hardware. As the owner of the equipment within your rack, you are responsible for its entire lifecycle, including maintenance and repair.
When a component like a drive or PSU fails, you have two options:
- Self-Service: Your personnel can travel to the data center with a replacement part and perform the swap.
- Remote Hands: You can open a ticket with the provider to use their “remote hands” service. An on-site technician will perform the physical work on your behalf for an hourly or per-incident fee. This is often the faster and more efficient option.
Ready to combine the control of bare metal with the security and connectivity of a world-class data center? ARPHost, LLC provides flexible and secure colocation services designed for businesses that demand performance and reliability. Explore our colocation solutions and build your ideal infrastructure today.


