A cloud computing security risk is any threat to the confidentiality, integrity, or availability of data and applications hosted in a cloud environment. These risks extend beyond sophisticated external attacks; they frequently originate from internal threats, human error, misconfigured infrastructure, weak access controls, and unpatched software vulnerabilities. This guide provides actionable, technical steps for mitigating these risks in private cloud and bare metal server environments.
Understanding Your Cloud Security Landscape
Migrating to a private cloud offers significant scalability and efficiency but expands the attack surface, creating new vectors for threat actors. Managing cloud security is not an auxiliary IT function—it is a core business operation essential for protecting organizational assets. Central to this is the shared responsibility model.
This model delineates security obligations between the cloud provider and the customer. For instance, when leasing bare metal servers in a secure data center, the provider is responsible for the physical security of the facility—access controls, surveillance, and environmental protections. The customer, however, is responsible for securing everything deployed on that hardware.
The Shared Responsibility Model in Practice
This division of labor is particularly critical in private cloud (IaaS) and bare metal hosting, where customers have extensive control and, consequently, greater security responsibility.
- Provider’s Responsibility: Securing the physical data center, networking hardware, and the underlying power and cooling infrastructure.
- Your Responsibility: Securing everything built upon that foundation. This includes configuring virtual machines (VMs), managing Identity and Access Management (IAM), encrypting data, implementing firewalls, and patching guest operating systems and applications.
The cloud is not inherently secure; security is a collaborative effort. The provider establishes a secure physical and network foundation, but you are responsible for constructing and maintaining a secure architecture on top of it. A failure in your responsibilities can negate the provider's security measures. For a deeper dive into these fundamentals, check out these broader cloud security insights.
To clarify responsibilities in an IaaS environment, such as a private cloud built on Proxmox VE, consider the following breakdown.
Quick Guide to Shared Responsibility in IaaS Environments
| Security Area | Cloud Provider Responsibility (e.g., Physical Security) | Customer Responsibility (e.g., IAM, Data Encryption) |
|---|---|---|
| Physical Security | Securing data centers, servers, and networking hardware. | N/A |
| Infrastructure | Managing the core network and virtualization layers. | Configuring virtual networks, firewalls, and load balancers. |
| Operating System | N/A (Customer manages the OS). | Patching, hardening, and securing the guest OS. |
| Applications | N/A | Securing application code and dependencies. |
| Data Security | N/A | Encrypting data at rest and in transit; managing data backups. |
| Identity & Access | N/A | Configuring IAM policies, roles, and user permissions. |
| Monitoring & Logging | Providing infrastructure logs. | Monitoring application logs, user activity, and security events. |
The greater the control—as with bare metal or private clouds—the more security responsibility shifts to the customer. While this offers greater flexibility, it demands rigorous security diligence.
Threat actors have adapted their tactics to target cloud environments. A staggering 82% of all data breaches involved data stored in the cloud, underscoring where the modern security battlefield lies. The financial impact is equally severe, with the average data breach costing businesses $4.76 million. This is not a hypothetical scenario but a clear and present danger that necessitates proactive risk management.
Identifying the Top 7 Cloud Security Threats
Understanding your security responsibilities is the first step; the next is identifying the specific threats targeting your infrastructure. A cloud computing security risk is often not a sophisticated zero-day exploit but a simple oversight with catastrophic consequences.
Here are the seven most common threats targeting private cloud and bare metal environments, with technical, real-world examples.
1. Cloud Misconfigurations
Cloud misconfiguration is the leading cause of security incidents. These are errors in the configuration of cloud resources that create unintended security vulnerabilities, often providing trivial entry points for attackers.
A classic example is an exposed S3-compatible object storage bucket where permissions are inadvertently set to "public." In a Proxmox VE environment, a common misconfiguration is creating an overly permissive firewall rule (allow all from any) at the datacenter level, which effectively nullifies all granular network segmentation rules for individual VMs.
By 2025, an estimated 99% of cloud security failures will be the customer’s fault, primarily due to misconfigurations. This is a critical vulnerability, as over 60% of organizations have already experienced a public cloud security incident, with misconfigurations as a leading cause. You can explore more cloud security statistics to understand the scale of this issue.
This is a direct reflection of the Shared Responsibility Model.
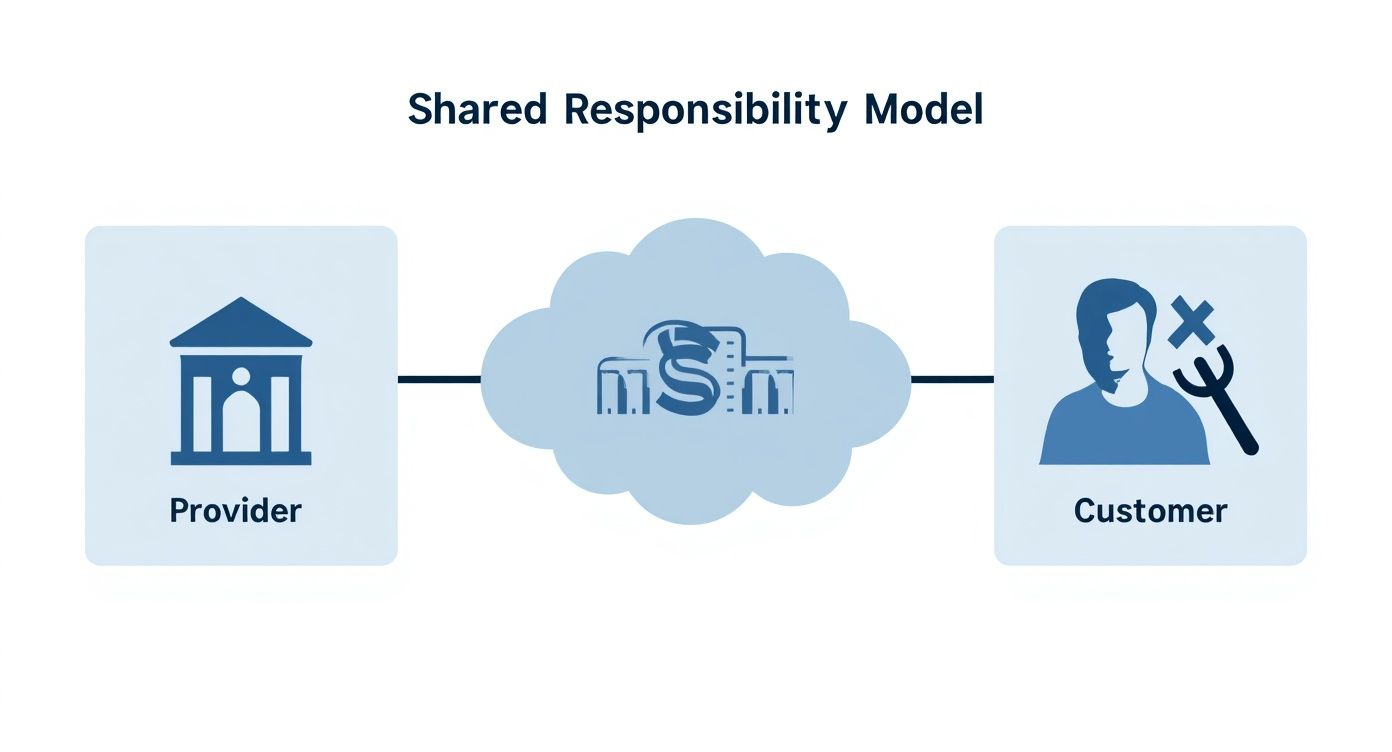
The model is unambiguous: while the provider secures the underlying infrastructure, you are responsible for the secure configuration of all resources deployed within it.
2. Data Breaches
Often a direct result of misconfiguration, a data breach is the unauthorized access and exfiltration of sensitive, protected, or confidential data. Attackers target high-value information, including personally identifiable information (PII), financial records, and intellectual property.
In a virtualized environment, an attacker might exploit an unpatched vulnerability (e.g., Log4Shell) in a web application running on a VM. From there, they could pivot to gain access to the underlying database server, exfiltrating data slowly over an extended period to evade detection.
3. Account Compromise
User accounts are the primary keys to your cloud infrastructure. Attackers employ tactics such as phishing, credential stuffing (reusing passwords from other breaches), and brute-force attacks to hijack user accounts, with a focus on those with administrative privileges.
A successful phishing attack on a system administrator could grant an attacker complete control over a Proxmox VE cluster. With these credentials, they could deploy ransomware, delete all VMs, or establish persistent, covert access for long-term espionage. This is why multi-factor authentication (MFA) is an essential security control.
4. Insecure APIs
APIs are the connective tissue of modern cloud environments, enabling programmatic interaction between services. If not properly secured, they become a significant liability.
An insecure API might lack proper authentication, allowing unauthenticated calls, or it could suffer from excessive data exposure, returning more information than necessary. For example, an internal API for managing VM resources, if accidentally exposed to the public internet without authentication, could allow an attacker to execute start, stop, or delete operations on production virtual machines.
Compromised APIs and user interfaces have seen a sharp rise, now accounting for 17.1% of observed incidents. This significant increase highlights a clear shift in attacker focus toward programmatic interfaces.
5. Insider Threats
An insider threat originates from within an organization, involving an individual with legitimate access—such as an employee, contractor, or partner. These threats can be malicious or accidental.
- Malicious Insider: A disgruntled system administrator could plant a logic bomb to delete critical backups after their departure.
- Accidental Insider: A junior DevOps engineer could mistakenly run a destructive automation script against the production environment instead of the staging environment, causing a major service outage or data loss.
6. Distributed Denial-of-Service (DDoS) Attacks
A DDoS attack aims to render a service unavailable by overwhelming it with a flood of malicious traffic from numerous distributed sources. For businesses reliant on cloud-hosted applications, a successful DDoS attack results in immediate downtime, financial loss, and reputational damage.
While most cloud providers offer baseline network-layer protection, sophisticated application-layer (L7) attacks can bypass these defenses and exhaust server resources (CPU, RAM), crippling services.
7. Supply Chain Attacks
In a supply chain attack, adversaries compromise a trusted third-party vendor or software provider. By injecting malicious code into a legitimate software update or management tool, they gain access to the systems of all the vendor's customers.
This attack vector is particularly dangerous because the malicious activity originates from a trusted source, often bypassing traditional perimeter security defenses.
Fortifying Access with Identity Management
The first and most critical line of defense against any cloud computing security risk is robust Identity and Access Management (IAM). Effective IAM is not merely about password management; it is about architecting a secure, accountable, and auditable environment based on defined policies.
The foundational concept of a strong IAM strategy is the Principle of Least Privilege (PoLP). This principle dictates that every user, application, or system should have the minimum level of permissions required to perform its function. Implementing PoLP drastically reduces the attack surface; if an account is compromised, the potential damage is contained to its limited permissions.
Implementing Least Privilege in Proxmox VE
Let's apply this principle in a practical scenario within a Proxmox VE private cloud. Consider a team with two roles: a junior administrator and a senior engineer. Their permissions must reflect their distinct responsibilities.
- Junior Admin Role: Requires the ability to start, stop, and access the console of development VMs. They should have no permissions to modify cluster settings, storage configurations, or production systems.
- Senior Engineer Role: Requires full administrative control to create VMs, manage virtual networking, and configure high-availability settings.
You can implement these granular roles directly within Proxmox VE using the command-line interface. First, define a role with limited privileges.
# Create a role named 'JuniorAdmin' with VM management permissions only
pveum roleadd JuniorAdmin -privs "VM.Audit VM.Console VM.PowerMgmt"
Next, create a user and assign this role for a specific resource path (e.g., a specific VM or a resource pool).
# Create a new user named 'dev-admin' within the Proxmox VE authentication realm
pveum useradd dev-admin@pve -comment "Junior Developer Admin"
# Assign the JuniorAdmin role to the dev-admin user for VM 101
pveum aclmod /vms/101 -user dev-admin@pve -role JuniorAdmin
This ensures the junior administrator can perform their duties without posing an unnecessary security risk to the broader infrastructure.
Why MFA Is Non-Negotiable
While PoLP limits post-breach damage, Multi-Factor Authentication (MFA) is a critical preventative control that stops unauthorized access in the first place. Relying solely on passwords is insufficient, as credentials are frequently compromised through phishing, credential stuffing, or other breaches.
MFA adds a second layer of verification—typically a time-based one-time password (TOTP) from an authenticator app—making it exponentially more difficult for an attacker to gain access, even with a valid password.
Implementing MFA is one of the most effective security controls available. It neutralizes the threat of compromised credentials, which remains a primary initial access vector for attackers.
Enabling MFA in Proxmox VE is a straightforward process and should be mandatory for all administrative accounts.
To enable MFA for a user:
- Navigate to Datacenter -> Permissions -> Two-Factor Authentication.
- Add a new TFA realm, selecting TOTP (Time-based One-Time Password). This method is compatible with standard authenticator applications like Google Authenticator or Authy.
- Individual users can then enable and configure their second factor under their personal user account settings.
By combining the granular control of PoLP with the robust defense of MFA, you establish a formidable barrier against unauthorized access, significantly mitigating a primary cloud computing security risk.
Implementing Data Protection and Encryption
While robust IAM secures access to your infrastructure, data protection and encryption safeguard the data itself. A comprehensive strategy to mitigate cloud computing security risk must protect data at all stages of its lifecycle: at rest (on storage media) and in transit (across the network).

This involves implementing cryptographic controls that render data unreadable to unauthorized parties, even if they bypass other security measures.
Encrypting Data at Rest on Bare Metal and Proxmox VE
Encrypting data at rest is a fundamental security requirement. For bare metal servers, the industry standard is Linux Unified Key Setup (LUKS), which provides full-disk encryption. LUKS creates an encrypted container for the entire operating system or specific data partitions, requiring a passphrase at boot time to decrypt the data.
This same level of protection can be extended to a Proxmox VE environment. While Proxmox VE does not directly manage guest-level encryption, it can be implemented within the guest OS using native tools like LUKS for Linux VMs or BitLocker for Windows VMs. This ensures that even if an attacker gains access to the underlying storage and exfiltrates a VM's virtual disk file, the data remains encrypted and inaccessible.
A comprehensive data protection plan must encompass the entire data lifecycle, including secure disposal of physical media. Utilizing secure data center decommissioning services is a critical final step to prevent data remnants from falling into the wrong hands.
Choosing the right encryption method requires balancing security requirements with performance considerations.
Encryption Methods for Private Cloud Environments
| Encryption Type | Best Use Case | Example Implementation | Performance Impact |
|---|---|---|---|
| Full-Disk Encryption (FDE) | Securing entire physical drives on bare metal servers. Protects against physical theft. | LUKS on Linux, BitLocker on Windows Server. | Minimal overhead on modern CPUs with AES-NI support. |
| Filesystem-Level Encryption | Encrypting specific directories or filesystems, often for multi-tenant environments. | eCryptFS or filesystem-native encryption like ZFS encryption. | Moderate, as encryption/decryption happens at the file I/O level. |
| Guest OS Encryption | Isolating VM data within a hypervisor environment like Proxmox VE. | Using LUKS inside a Linux VM or BitLocker inside a Windows VM. | Varies by guest OS; generally low impact with modern virtualization. |
| Application-Level Encryption | Securing specific data fields within a database or application. | Encrypting sensitive columns in a MySQL/PostgreSQL database using application logic. | High, as it requires specific code and can impact query performance. |
In high-security environments, a defense-in-depth strategy often combines multiple encryption methods.
The Ultimate Defense: Immutable Backups
Encryption protects data from unauthorized access, but it does not prevent its deletion. An attacker with administrative credentials can delete encrypted data as easily as unencrypted data. This is where immutable backups provide a critical last line of defense.
"Immutable" means unchangeable. Once an immutable backup is written, it cannot be modified, overwritten, or deleted for a predefined retention period, even by an administrator with root privileges. This creates a secure, air-gapped copy of your data that is resilient to ransomware, which often targets and encrypts backups before attacking production systems.
A Strategy for Encrypted Immutable Backups
Implementing a robust, encrypted, and immutable backup strategy is one of the most effective measures for reducing cloud computing security risk. Here is a proven methodology for Proxmox VE environments:
- Select an Appropriate Tool: Use a backup solution with native support for immutability and client-side encryption. Proxmox Backup Server is an ideal choice, as it integrates seamlessly with Proxmox VE and performs strong, client-side encryption on the hypervisor before data is transmitted to the backup server.
- Implement Off-Site Storage: Adhere to the 3-2-1 backup rule: maintain three copies of your data on two different media types, with at least one copy stored off-site. Immutable backups should be replicated to a geographically separate location, such as a secondary data center or a secure, S3-compatible object storage repository with object lock capabilities.
- Define Immutability Policies: Configure retention policies based on business and compliance requirements. For example, set daily backups to be immutable for 30 days, ensuring a guaranteed recovery window.
- Automate and Test Rigorously: Automate the entire backup and replication process. Crucially, schedule regular, automated recovery drills to validate the integrity of your backups and ensure your team can execute the disaster recovery plan effectively.
Combining strong encryption with a layered, frequently tested immutable backup strategy builds true cyber resilience. Explore effective immutable backup solutions to learn how to architect systems capable of withstanding modern threats.
Securing Your Network with Segmentation and Monitoring
A robust network security posture is fundamental to mitigating cloud computing security risk. An effective strategy involves creating isolated internal compartments—a concept known as network segmentation—and maintaining constant visibility through proactive monitoring.
Think of a private cloud as a ship with multiple watertight compartments. A breach in one compartment is contained, preventing the entire vessel from sinking.
Creating Virtual Fortresses with Network Segmentation
Network segmentation is the practice of dividing a network into smaller, isolated sub-networks or segments. This dramatically limits an attacker's lateral movement capabilities. If a VM is compromised, the attacker is confined to that segment, unable to access critical systems in other segments, such as production databases or management interfaces.
In a Proxmox VE environment, this is achieved using VLANs (Virtual Local Area Networks), which allow you to create distinct logical networks on the same physical infrastructure.
- Production VLAN: For live, customer-facing applications and databases. Access is highly restricted.
- Development VLAN: A sandbox for developers to work without risk to production systems.
- Management VLAN: A dedicated, isolated network for administrative access to hypervisor hosts and network hardware.
This logical separation is a powerful security control. A breach in the development environment is contained and cannot spread to production.
Layering Firewalls for Defense in Depth
Once the network is segmented, you must enforce strict traffic policies between zones using firewalls. A multi-layered firewall strategy provides the most effective defense.
A well-segmented network with layered firewalls provides an active defense. It not only prevents unauthorized access but also contains and slows down attackers who breach the perimeter, providing valuable time for detection and response.
First, configure the Proxmox VE firewall, which operates at the hypervisor level. It enables the creation of granular, stateful firewall rules for each VM and container, controlling traffic at its source.
Next, implement controls on your physical network hardware. Enterprise-grade devices like Juniper Network Device Best Practices routers and switches allow for the enforcement of strict inter-VLAN routing policies and Access Control Lists (ACLs). This provides a critical secondary layer of defense, ensuring that a misconfiguration at the hypervisor level does not compromise network security. For more on this, review our guide on how to secure a web server.
Proactive Monitoring and Centralized Logging
Segmentation and firewalls are your static defenses; monitoring and logging provide the necessary visibility to detect and respond to threats. Without comprehensive logging, you are operating blindly.
Effective monitoring requires logging high-value security events that indicate potential malicious activity.
Key Events to Log and Alert On
- API Calls: Log all administrative actions, especially those related to the creation, deletion, or modification of VMs, storage, and user permissions.
- Login Attempts: Monitor all successful and failed login attempts, particularly for privileged accounts. A high volume of failed logins from a single IP address is a strong indicator of a brute-force attack.
- Administrative Changes: Log all changes to firewall rules, user roles, network configurations, and other security settings.
- System-Level Events: Monitor critical OS-level events within VMs, such as unexpected software installations or privilege escalation attempts (
sudocommands).
These logs must be aggregated in a centralized logging solution (e.g., an ELK Stack or Graylog) to prevent tampering and facilitate analysis. Centralized logging provides a single pane of glass to correlate events across your entire infrastructure, enabling the detection of sophisticated, coordinated attacks.
How Managed Services Take Cloud Security Risks Off Your Plate
Managing cloud security demands continuous vigilance, specialized expertise, and significant resources. A managed services provider (MSP) acts as a dedicated security partner, assuming the operational burden of defending your infrastructure.
This partnership transforms your security posture from reactive to proactive, leveraging specialized knowledge to mitigate a significant portion of your cloud computing security risk.
Gaining an Expert Security Operations Team
An MSP provides immediate access to a team of security professionals who specialize in infrastructure management. They handle critical but time-consuming tasks, including:
- Proactive Threat Monitoring: 24/7 monitoring of infrastructure for suspicious activity using advanced security tools.
- Expert Firewall Configuration: Implementing and maintaining complex firewall rules on devices like Juniper routers and within the Proxmox VE hypervisor to enforce network segmentation.
- Consistent Patch Management: Ensuring all systems—from the hypervisor to guest operating systems—are patched promptly to protect against known vulnerabilities.
- Robust Backup and Disaster Recovery: Designing, implementing, and regularly testing resilient backup strategies, including encrypted, immutable backups to ensure recovery from ransomware.
Partnering with an MSP offloads the daily operational security tasks, freeing your internal IT team to focus on strategic initiatives that drive business value, confident that the underlying infrastructure is managed according to industry best practices.
A Real-World Scenario in Action
Consider an e-commerce company running its platform on a managed private cloud. Its internal IT team is focused on application development and enhancing the customer experience. Without an MSP, this team would also be responsible for patching hypervisors, analyzing network logs, and verifying backup integrity.
By outsourcing these responsibilities, they avoid common misconfigurations that lead to breaches. The MSP ensures their cloud environment is hardened, access controls adhere to the principle of least privilege, and their disaster recovery plan is a tested, operational process.
This model is particularly beneficial for organizations seeking enterprise-grade security without the significant overhead of an in-house security operations center (SOC). Exploring managed IT services for small business offers a clear path to a stronger security posture.
Common Questions About Cloud Security
Here are answers to common questions from system administrators and IT leaders managing private cloud environments.
What’s The Single Biggest Security Risk For A Small Business?
The single biggest security risk is human error leading to misconfiguration. This includes publicly exposed storage, weak or reused passwords on administrative accounts, and overly permissive IAM roles.
These are not sophisticated attacks but fundamental security oversights. Automated scanners constantly search for these vulnerabilities, making robust Identity and Access Management (IAM) policies and regular security audits your most effective defense.
How Does a Private Cloud Shift My Security Duties?
Adopting a private cloud on bare metal using a platform like Proxmox VE provides greater control but also shifts more security responsibility to you. While the hosting provider secures the physical data center, you are responsible for securing the entire stack from the hypervisor upward.
This includes securing VMs, guest operating systems, virtual networking, applications, and data. This requires a proactive approach to network segmentation, patch management, and implementing a comprehensive, tested backup and disaster recovery strategy.
With a private cloud, greater control comes with greater responsibility. The shared responsibility model leans heavily your way, turning security from a checkbox item into a core part of your daily operations.
I Already Have Backups. Are Immutable Ones Really Necessary?
Yes. Standard backups are vulnerable to modern ransomware, which is designed to encrypt or delete them before attacking production data, thereby eliminating your ability to recover.
Immutable backups are fundamentally different. They are "write-once, read-many," meaning once a backup is created, it cannot be altered or deleted for a predefined period. Even an attacker with full administrative access cannot compromise this clean, uncorrupted copy of your data, making it an essential defense against ransomware.
Mitigating your cloud computing security risk is not a one-time project but a continuous, layered process. At ARPHost, LLC, we help businesses build resilient and secure infrastructure with managed private clouds, encrypted immutable backups, and proactive monitoring. Learn more about our managed hosting and security solutions to see how we can help.



[…] Cloud services: If your ePHI lives in the cloud, you have to account for it. This includes everything from file storage and email hosting to your telehealth platform, all while mitigating cloud computing security risks. […]