A STUN (Session Traversal Utilities for NAT) server is a fundamental component in modern real-time communication architectures, designed to solve a critical networking problem: enabling direct peer-to-peer connections between devices operating behind Network Address Translation (NAT) routers.
For IT professionals managing VoIP, WebRTC, or other real-time services, a STUN server acts as a simple public address discovery service. A device on a private network (e.g., behind a corporate firewall) sends a request to a public-facing STUN server. The server inspects the packet’s source IP address and port, which have been rewritten by the NAT device, and sends this public address information back to the client.
This process is the cornerstone of efficient peer-to-peer (P2P) communication.
How STUN Enables High-Performance Networking
When a client initiates a VoIP call or a WebRTC session, establishing a direct media path to the remote peer is the primary goal. To achieve this, the client sends a lightweight “binding request” to a configured STUN server.
The server’s function is purely informational. It examines the source IP and port of the incoming request and reflects this data back to the client in a “binding response.” Armed with its public, routable address (known as the Server Reflexive Candidate), the client can now share this information with the other peer via signaling to establish a direct P2P media flow.
This direct path is crucial for performance. Without it, all media packets would require relaying through an intermediary server (like a TURN server), which introduces latency, increases bandwidth costs, and adds a potential point of failure. For demanding applications like the intricacies of 24/7 live streaming, a low-latency, direct connection is a non-negotiable requirement for service quality.
The Role of STUN in Modern Communication Protocols
Standardized in RFC 5389, STUN is a lightweight protocol that allows an endpoint behind a NAT to discover its public IP address and the type of NAT it is behind. This discovery process is what makes efficient P2P connections possible, improving the performance and reliability of countless real-time services.
This capability is the bedrock of modern enterprise communication systems. For organizations deploying robust infrastructure, a deep understanding of STUN is essential for architecting effective small business VoIP solutions and private cloud communication platforms.
STUN Server Core Concepts at a Glance
This table summarizes the essential terminology and purpose of STUN, making it easy to grasp how it fits into network architecture.
| Concept | Description | Primary Function |
|---|---|---|
| STUN | Session Traversal Utilities for NAT | A protocol that helps devices find their public IP address and port from behind a NAT router. |
| NAT | Network Address Translation | A method used by routers to map multiple private IP addresses to a single public IP address. |
| Public IP Address | The single, unique address assigned by an ISP that identifies a device on the public internet. | To allow devices outside the local network to find and communicate with a specific device. |
| P2P Connection | Peer-to-Peer Connection | A direct communication link between two devices without needing a central relay server. |
Ultimately, STUN performs the initial address discovery so that services like VoIP and video chat can connect peers directly and efficiently, forming a foundational layer for high-performance virtual server management and communication.
Understanding the STUN Discovery Process Step by Step
To fully grasp what a STUN server does, it’s useful to analyze the packet flow from a client to the server. The entire exchange is a simple, efficient query-response mechanism designed to reveal one critical piece of information: a client’s public IP address and port mapping.
Let’s use a common technical scenario: two clients initiating a WebRTC video session from browsers within separate private networks.
The process begins when Client A’s browser attempts to establish a connection with Client B. The challenge is that Client A only knows its private IP address (e.g., 192.168.1.100), which is non-routable on the public internet and useless for Client B.
To discover its public identity, Client A’s browser sends a small UDP packet, known as a binding request, to a pre-configured STUN server on the public internet. These servers are optimized to handle a high volume of these simple requests.
This flow chart illustrates the core address translation problem that STUN is designed to solve.
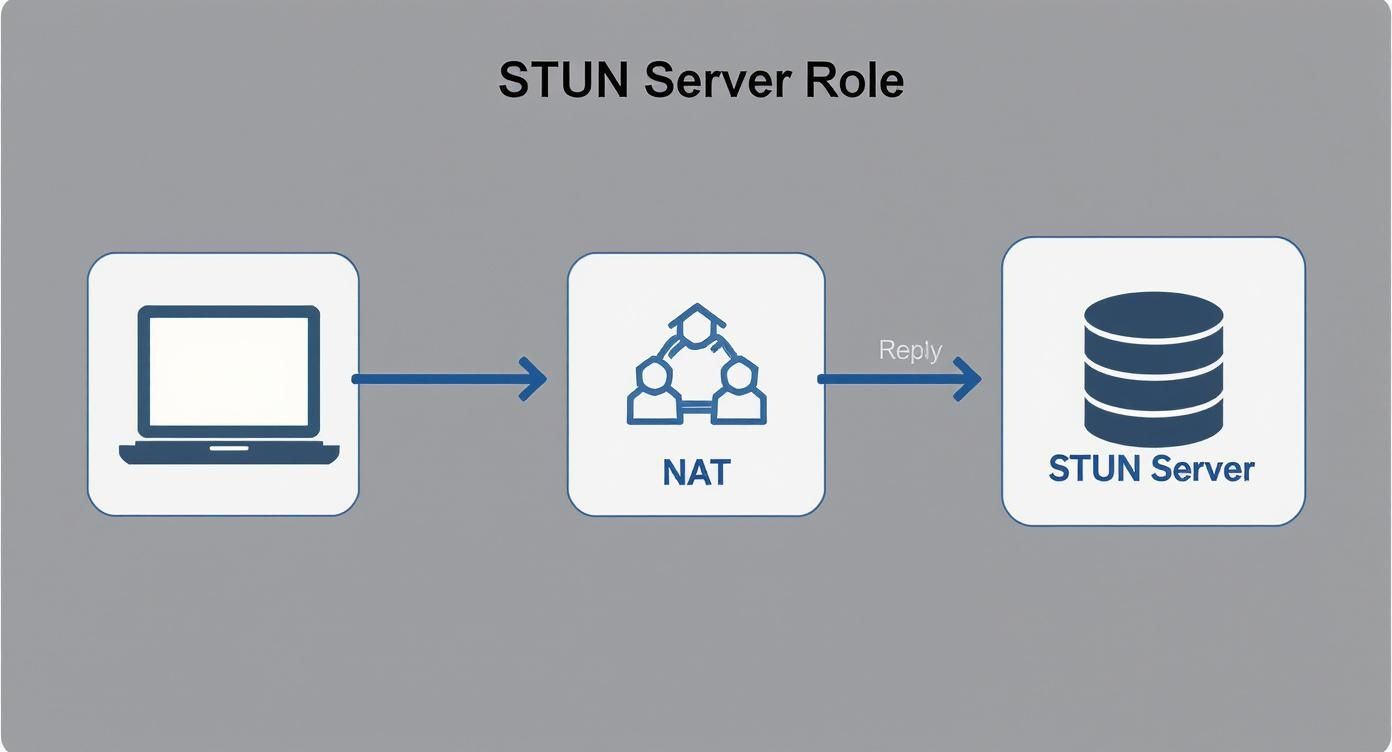
This NAT-induced address modification is the fundamental reason STUN is a necessity in P2P architectures.
The Server’s Role and the Binding Response
When the STUN server receives the binding request, its logic is straightforward. It inspects the source IP address and source port from the IP/UDP headers of the incoming packet. This source information represents the public-facing endpoint created by the NAT router.
The server then constructs a binding response packet, embedding this public IP and port (the server reflexive address) into its payload, and sends it back to the client’s original IP and port. Once Client A receives this response, it now knows its public address and can use a signaling server to share it with Client B to initiate a direct P2P connection.
Key Takeaway: A STUN server is a discovery utility, not a media relay. It facilitates the initial P2P handshake by providing address information but does not process or forward any of the subsequent audio, video, or data streams. All media traffic flows directly between peers whenever possible.
Seeing It in Action with a CLI Command
For system administrators and network engineers, this process can be verified directly from the command line. Using a tool like stun-client (part of the stun-client or coturn-client package), you can query a public STUN server.
Execute the following command in a Linux terminal to query one of Google’s public STUN servers:
# Example using stun-client to query a public STUN server
stunclient stun.l.google.com 19302
Running this command sends a binding request and returns a response containing the public IP and port as seen by the STUN server, providing a practical demonstration of the protocol in action.
How STUN Navigates Different NAT Types
A STUN server’s effectiveness is entirely dependent on the behavior of the NAT device it must traverse. For IT professionals deploying and managing VoIP or real-time communication infrastructure, understanding NAT types is critical for diagnosing connectivity issues and architecting reliable networks.
STUN operates on the assumption that a NAT device will create a port mapping that is predictable and reusable. When a client sends a packet to an external destination, the NAT maps its private IP:port to a public IP:port. STUN works if this public mapping can be used by another peer to send inbound traffic back to the client.

Predictable NATs STUN Can Handle
STUN is generally successful with NATs that maintain consistent external IP and port mappings. This means the public address discovered via the STUN server is a valid destination for other peers.
These are the most common “STUN-friendly” NAT types:
- Full Cone NAT: The least restrictive. Once an internal IP:port is mapped to a public IP:port, any external host can send packets to that public mapping to reach the internal client.
- Restricted Cone NAT: More restrictive. An external host can only send packets to the internal client if the client has previously sent a packet to that host’s IP address.
- Port Restricted Cone NAT: The most restrictive of the “cone” types. An external host can only send packets to the internal client from the specific source port that the client originally sent traffic to.
Despite their differences, STUN works with these NATs because the external IP:port pair remains constant for subsequent connections.
Why Symmetric NAT Breaks STUN
The primary obstacle for STUN is Symmetric NAT. This NAT type is highly restrictive and violates the core assumption STUN relies on. When a client behind a Symmetric NAT sends a packet to a specific destination (e.g., a STUN server), the router creates a unique, destination-specific public IP and port mapping.
If that same client then attempts to communicate with a different destination (e.g., another peer in a video call), the NAT router generates a completely new and different public port mapping for that session.
This behavior renders the address obtained from the STUN server useless for connecting to any other peer. The discovered address is only valid for communication back to the STUN server itself, making a direct P2P connection impossible.
This limitation is why STUN is not a complete NAT traversal solution. When encountering a Symmetric NAT, a fallback mechanism is required. This is where protocols like TURN (Traversal Using Relays around NAT) are essential, typically managed within the ICE (Interactive Connectivity Establishment) framework, which orchestrates the entire connectivity process.
A direct, STUN-enabled connection can reduce media latency by up to 50% and lower bandwidth consumption by over 30% compared to a relayed connection. To dig deeper, you can discover more insights about STUN on Wikipedia.
STUN Servers in Real-World Architectures
Moving from theory to practice, STUN servers are a critical infrastructure component configured in production systems to ensure reliable real-time communication.
Its most prominent application is in WebRTC (Web Real-Time Communication), the open-source framework that enables real-time video, voice, and data sharing directly within web browsers. When a WebRTC session is initiated, the browser executes the Interactive Connectivity Establishment (ICE) protocol to find the most efficient network path to other peers.
The first step in the ICE process is to gather “candidates,” or potential addresses, for a connection. This begins with a query to a STUN server.
WebRTC and Automated Discovery
In WebRTC implementations, STUN server addresses are explicitly defined in the client-side application code within the RTCPeerConnection configuration. This tells the browser where to send its binding requests.
A standard JavaScript configuration for an RTCPeerConnection in a bare metal or private cloud environment would look like this:
const configuration = {
iceServers: [
{
urls: 'stun:stun.your-domain.com:3478'
},
{
urls: 'stun:stun.l.google.com:19302' // Public fallback
}
]
};
const peerConnection = new RTCPeerConnection(configuration);
This configuration enables direct P2P connections, which are essential for minimizing latency and reducing the operational load on central servers, aligning with best practices for scalable and performant virtual server management.
VoIP and Unified Communications Systems
Beyond WebRTC, STUN is indispensable for Voice over IP (VoIP) systems and communications platforms like Asterisk, FreeSWITCH, or Kamailio. Most SIP (Session Initiation Protocol) endpoints, such as IP phones and soft clients, reside on private networks, making them unreachable from the public internet without NAT traversal.
By configuring a STUN server address in a SIP client, the client can discover its public IP address and embed it into the Contact headers of SIP messages and the connection information within SDP (Session Description Protocol) payloads. This is a mandatory step for successful call setup and media negotiation, a process detailed further in our guide on how SIP trunking works.
For architects designing modern communications platforms, proper STUN implementation is a key piece of building scalable and resilient microservices architectures. When foundational components like STUN are correctly deployed, they contribute to a high-performance, fault-tolerant system that functions reliably across diverse network environments.
How to Deploy a Private STUN Server with Coturn
For enterprise and commercial applications, relying on public STUN servers introduces unacceptable risks related to availability, performance, and security. While public servers are suitable for testing, production environments demand the control and reliability of dedicated infrastructure. For a deeper analysis, see this overview of STUN servers.
Fortunately, deploying a private STUN server is a straightforward process. This guide provides a step-by-step tutorial for setting up a secure, STUN-only instance using coturn—a robust, open-source TURN/STUN server implementation—on a Linux virtual server. This approach provides full control over your NAT traversal infrastructure, whether deployed on a bare metal server or within a Proxmox VE environment.

Step 1: Provision a Linux Server and Install Coturn
Begin by provisioning a minimal Linux server. A lightweight distribution like Debian 12 or Ubuntu 22.04 LTS is ideal, as coturn has minimal dependencies. A KVM-based virtual machine with 1 vCPU and 512MB of RAM is sufficient for a dedicated STUN server.
Connect to your server via SSH and install coturn using the system’s package manager:
# Update package lists and install coturn
sudo apt-get update
sudo apt-get install coturn -y
Next, enable the coturn service to start on boot. Edit the configuration file /etc/default/coturn and uncomment the TURNSERVER_ENABLED=1 line:
# Use sed to enable the service automatically
sudo sed -i 's/#TURNSERVER_ENABLED=1/TURNSERVER_ENABLED=1/' /etc/default/coturn
Step 2: Configure a Secure, STUN-Only Instance
The primary configuration file is /etc/turnserver.conf. For a STUN-only deployment, you must disable the resource-intensive TURN relaying functionality.
Create a minimal turnserver.conf with the following parameters. Replace your-server-ip with your server’s public IP address and your-domain.com with your organization’s domain.
# /etc/turnserver.conf
# Listening port for STUN requests
listening-port=3478
# Specify the public IP address of the server
external-ip=your-server-ip
# Enable message integrity checking
fingerprint
# Disable TURN relaying functionality
no-multicast-peers
no-loopback-peers
no-tcp-relay
no-tls
no-dtls
# Disable authentication, as it's not needed for STUN
no-auth
# Define the server's realm
realm=your-domain.com
# Log to a dedicated file instead of stdout
log-file=/var/log/coturn.log
no-stdout-log
Best Practice: Implement strict firewall rules. Any internet-facing server is a potential target. Configure your firewall (e.g.,
ufwor Juniper SRX) to allow inbound traffic only on UDP port 3478 from trusted sources if possible. A minimal attack surface is a core principle of network security.
This configuration is foundational for any organization deploying its own VoIP infrastructure, such as when selecting a cloud PBX provider or building a custom solution.
Step 3: Start and Verify the Service
After saving your configuration, start and enable the coturn service:
sudo systemctl start coturn
sudo systemctl enable coturn
To verify that the server is operational, use a STUN client from a different machine to query your new server. If it returns the correct public IP address, your private STUN server is successfully deployed.
Common Questions About STUN Servers
Here are answers to common technical questions IT professionals encounter when implementing STUN within their infrastructure.
Does a STUN Server Handle Media Traffic?
No. A STUN server’s role is strictly limited to the initial address discovery phase. It helps a client determine its public IP address and port (its server reflexive candidate).
Once this discovery is complete and a P2P connection is established, all media packets (audio, video) flow directly between the peers. The STUN server is no longer involved in the session, which is why the protocol is exceptionally lightweight and scalable.
What Is the Difference Between STUN and TURN?
STUN and TURN are both NAT traversal protocols used by the ICE framework, but they serve distinct functions:
- STUN is the primary mechanism. It attempts to facilitate a direct P2P connection by discovering a client’s public IP address. It is lightweight and efficient but fails in the presence of Symmetric NAT.
- TURN (Traversal Using Relays around NAT) is the fallback mechanism. When a direct P2P connection cannot be established, a TURN server acts as a media relay, forwarding all packets between the peers.
While TURN guarantees connectivity even in the most restrictive network environments, it comes at a significant cost. Relaying traffic increases latency, consumes substantial server CPU and bandwidth resources, and introduces a centralized point of failure.
Are Public STUN Servers Secure for Enterprise Use?
For development, testing, or non-critical applications, public STUN servers are acceptable. However, they are not suitable for enterprise or commercial use. Relying on a third-party service introduces significant risks, including lack of availability (no SLA), unpredictable performance, and potential security vulnerabilities.
For any production system, deploying a private STUN/TURN server on dedicated infrastructure is the industry best practice. This ensures full control over reliability, security, and performance, which is non-negotiable for business-critical managed IT services.
Do I Need STUN If I Am Not Using NAT?
No. If a device has a publicly routable IP address and is not behind a NAT or a restrictive firewall, a STUN server is unnecessary. The device already knows its public address and can provide it directly to peers during signaling to establish a connection.
STUN was designed exclusively to solve the address discovery problem for clients located behind NAT devices. In environments with public IP addressing, the problem STUN solves does not exist.
Ready to build a robust, high-performance IT infrastructure? At ARPHost, LLC, we provide the bare metal servers, private cloud solutions, and managed services you need to scale with confidence. Explore our hosting solutions today!