The weak spots in cloud computing can be as simple as human error—a sloppy misconfiguration—or as complex as hypervisor escapes and compromised supply chains. Each of these creates an open door for attackers, leading to major data breaches, crippling downtime, and serious financial pain. A proactive security plan isn't just nice to have; it's essential for any business leveraging cloud infrastructure.
Defining the Modern Cloud Threat Landscape

The cloud powers modern business, but its fast-paced nature creates security problems that old-school, perimeter-based defenses were never built to solve. To effectively mitigate the vulnerabilities of cloud computing, IT professionals must look past the buzzwords and focus on the real threats impacting infrastructure daily.
This begins with a security-first mindset, one that acknowledges the challenges of the shared responsibility model. This model, where the cloud provider secures the cloud itself and you secure what you put in it, often creates a dangerous gray area. While the provider manages the physical hardware, your organization is on the hook for securing your data, applications, and access configurations. This is precisely where most security failures happen.
A New Security Approach Isn't Optional
The fallout from these failures is escalating. A staggering 80% of companies experienced a cloud security breach in the last year alone. The financial impact is just as severe—the average cost of a data breach has ballooned to $4.35 million globally, and it jumps to a painful $10.22 million in the United States.
These numbers tell a clear story: a reactive security posture is no longer viable. You need to build defenses from the infrastructure up, creating a security posture that’s proactive, not reactive. Understanding how security is handled in different cloud setups, like those in a Guide to Cloud-Based Contact Centre Solutions, can offer valuable perspective on this evolving challenge.
To get a clearer picture of what’s at stake, let's break down the most common cloud vulnerabilities and their tangible business impact.
Top Cloud Vulnerabilities and Their Business Impact
| Vulnerability Category | Common Example | Primary Business Risk | How ARPHost Mitigates |
|---|---|---|---|
| Misconfiguration | Publicly accessible storage or open database ports. | Data breaches, compliance fines, reputational damage. | Fully Managed IT Services with hardened, best-practice configurations. |
| Identity & Access | Over-privileged accounts or weak password policies. | Unauthorized access, account takeover, lateral movement. | Managed access controls and proactive monitoring to enforce least privilege. |
| Network Security | Poorly configured security groups or lack of segmentation. | Malware propagation, denial-of-service attacks. | Managed Juniper network devices and strict firewall rule management. |
| Data Leakage | Unencrypted data in transit or at rest. | Sensitive data exposure, intellectual property theft. | Offsite, encrypted backups and secure network configurations. |
| Insider Threats | A disgruntled employee abusing their access rights. | Data theft, sabotage of critical systems, financial fraud. | Granular permissions in Proxmox Private Clouds and audit logging. |
| Supply Chain | A compromised third-party library or service. | Widespread system compromise, loss of customer trust. | Secure Web Hosting Bundles with vetted components like CloudLinux OS. |
This table only scratches the surface, but it highlights how seemingly small oversights can spiral into massive business problems. The interconnected nature of cloud services means one weak link can expose the entire chain.
The core challenge isn't the cloud itself, but how we secure it. The sheer speed of deployment and the complexity of modern cloud services can easily outrun a company's ability to lock them down, leaving a trail of misconfigurations and overlooked attack vectors.
This guide will break down the most common vulnerabilities of cloud computing, offering actionable examples and solutions to strengthen your defenses. We'll also explore how partnering with a managed service provider like ARPHost turns security from a constant headache into a reliable, managed strength.
Misconfigurations: The Unlocked Digital Front Door

One of the most persistent and dangerous vulnerabilities of cloud computing isn't a shadowy hacker group or a sophisticated zero-day exploit. It's simple human error. Cloud misconfigurations are the digital equivalent of leaving your front door wide open. It’s no surprise that a staggering 1 in 3 easily exploitable vulnerabilities on cloud assets trace back to these preventable mistakes.
These errors often creep in because default settings on cloud services are built for convenience, not Fort Knox-level security. An engineer, rushing to get a new app online, might accidentally leave a storage bucket publicly accessible or set up a database to accept connections from anywhere in the world. These aren't malicious acts, but the consequences can be just as devastating as a targeted cyberattack.
For example, a misconfigured firewall rule on a virtual server can expose critical internal services to the public internet. This can be as simple as allowing SSH access from 0.0.0.0/0.
How to Fix It (The Hard Way): A Step-by-Step CLI Example
- Identify the Open Port: Use a tool like
nmapto scan your public IP for open ports.nmap -p 22 YOUR_SERVER_IP - Check Firewall Rules: Log into your server and check the current
iptablesrules.sudo iptables -L # Look for a rule allowing access to port 22 from anywhere - Correct the Rule: Replace the overly permissive rule with one that only allows access from a specific, trusted IP address (e.g., your office IP).
# First, delete the old rule (e.g., if it's rule number 5 in the INPUT chain) sudo iptables -D INPUT 5 # Then, add a new, specific rule sudo iptables -A INPUT -p tcp -s YOUR_OFFICE_IP/32 --dport 22 -j ACCEPT - Save the Rules: Ensure the rules persist after a reboot.
sudo service iptables save
The Identity and Access Management Dilemma
Beyond open ports, the next major battleground is Identity and Access Management (IAM). A sloppy IAM policy is one of the fastest ways to hand an attacker the keys to the kingdom. Common IAM blunders include:
- Overly Permissive Roles: Giving a user "administrator" privileges when they only need read-only access.
- Stale or Orphaned Accounts: Forgetting to disable accounts for former employees or retired applications, leaving unmonitored backdoors.
- No Multi-Factor Authentication (MFA): Failing to require MFA on administrative accounts leaves them vulnerable to credential stuffing.
In sprawling public cloud environments, tracking thousands of permissions across hundreds of services becomes a monumental task. An attacker with a single over-privileged account can move laterally, escalate access, and steal data. Automating configurations is a critical defense, and you can learn more by reviewing our Infrastructure as Code best practices.
Scaling This with ARPHost
This is exactly where a managed security model proves its worth. Instead of forcing your team to become expert auditors, ARPHost provides environments that are secure from the ground up. Our fully managed IT services take the guesswork out of the equation by implementing hardened, best-practice configurations from day one. When you partner with us, our experts proactively manage your infrastructure, ensuring firewall rules follow the principle of least privilege and access controls are locked down.
For businesses that need robust, isolated environments, our Dedicated Proxmox Private Clouds offer a powerful solution. You get the security of single-tenant hardware combined with our expert management, effectively closing the door on the entire class of misconfiguration vulnerabilities that plague public cloud users.
Ready to lock down your infrastructure? Start with our $5.99/month VPS at arphost.com/vps-hosting/.
Hypervisor Escapes and Tenant Isolation Failures
In a public cloud, your virtual server is just one of many "tenants" running on the same physical hardware. The security of your entire operation depends on a thin digital wall called the hypervisor. This critical software is responsible for keeping every tenant's resources—CPU, memory, storage—completely separate.
Think of a public cloud as a massive apartment building. The hypervisor is supposed to be the walls and locks separating your unit from everyone else's. A hypervisor escape is the digital equivalent of a neighbor breaking through a shared wall. It's a catastrophic flaw where an attacker in one virtual machine (VM) exploits a bug in the hypervisor to "escape" their isolated bubble and gain access to the underlying host server or even other tenants' VMs. This is one of the most severe vulnerabilities of cloud computing because it shatters the foundation of multi-tenant architecture.
The Real-World Risk of Shared Hardware
This isn’t just theoretical. Processor vulnerabilities like Spectre and Meltdown demonstrated how side-channel attacks could allow one process to read the memory of another, crossing tenant boundaries. While cloud providers scrambled to patch their systems, these events were a harsh reminder that when you share hardware, you also share risk.
The core problem with multi-tenancy is shared fate. Your security is only as strong as the hypervisor software and the actions of every other anonymous tenant on the same physical machine. A single flaw can create a domino effect.
For businesses handling sensitive data, financial records, or intellectual property, this shared risk is often unacceptable. Relying on a third party to perfectly maintain the digital walls between you and potentially malicious actors introduces a level of uncertainty that can violate compliance standards. Understanding these foundational threats is a key part of implementing robust, multi-layered security. You can learn more in our detailed overview of the essential layers of security.
This is where the argument for a private cloud becomes undeniable.
The Proxmox Private Cloud Solution
The only surefire way to eliminate the risk of a tenant isolation failure is to get rid of the other tenants. This is the fundamental security advantage of a dedicated, single-tenant environment.
With ARPHost's Dedicated Proxmox Private Clouds, you are the sole occupant of the "building." We provide you with your own dedicated bare metal servers, which means your hypervisor manages only your virtual machines. There are no other tenants and no shared resources, eliminating the possibility of a "noisy neighbor" breaking through the wall.
This screenshot of the Proxmox VE management interface shows the direct control you gain over your dedicated environment, from VMs and containers to storage and networking.

By providing full root access to dedicated hardware, we empower you to build a truly isolated and secure infrastructure, free from the inherent risks of public cloud multi-tenancy.
Our Proxmox-based private clouds give you:
- Complete Resource Isolation: Your CPUs, RAM, and storage are yours alone.
- Enhanced Security Control: You have full authority over your virtual network, firewall rules, and security policies.
- Performance Guarantees: No "noisy neighbors" can consume resources and slow down your applications.
By moving to a single-tenant model, you effectively neutralize an entire class of cloud vulnerabilities. Explore our Dedicated Proxmox Private Cloud plans starting at $299/month.
Securing Your APIs and Supply Chain
Your cloud environment isn’t an island. It's connected to dozens of other services through a web of Application Programming Interfaces (APIs) and third-party code. While this interconnectedness makes modern applications powerful, it also opens up a massive attack surface.
Insecure APIs are one of the most common and dangerous vulnerabilities of cloud computing. Think of an API as a digital waiter taking orders between software systems. If that waiter doesn't check IDs or verify orders, they could be tricked into handing over sensitive data or bringing the entire kitchen to a halt with bogus requests. Attackers constantly probe for these weak points, such as a lack of rate limiting or improper authentication, turning a trusted connection into a backdoor for data exfiltration or denial-of-service (DoS) attacks.
The Escalating Threat of Supply Chain Compromises
Even more sinister is the software supply chain compromise. Your applications are assembled using a mix of open-source libraries and frameworks. If an attacker sneaks malicious code into one of these widely used components, they can compromise every application that depends on it.
It's like a single contaminated ingredient making its way into thousands of restaurant meals. We’ve seen high-profile breaches prove just how devastating this can be, giving attackers a trusted, inside track that bypasses most traditional defenses.
The stats tell a sobering story. As threats like ransomware get more sophisticated, attackers are hitting these external trust relationships hard. Between 2022 and 2023, breaches in cloud environments shot up by 75%. Digging deeper, supply chain compromises now rank as the second most common attack vector, accounting for 15% of breaches and costing an average of $4.91 million per incident. You can find more details in the latest data breach report.
The modern application is a complex assembly of first-party and third-party code. A supply chain attack exploits the inherent trust we place in our software dependencies, turning a trusted component into a Trojan horse.
Mitigating External Threats with Managed Security
Fighting back requires more than securing your own code. It means rigorously vetting third-party components, staying on top of patching, and locking down your network to limit the blast radius. This is a full-time job where a managed security approach makes all the difference.
ARPHost's fully managed IT services are designed to tackle these exact vulnerabilities head-on. Our expert team shoulders the burden of continuous security management, giving you a powerful defense against both API and supply chain attacks.
Here’s how we lock down your environment:
- Rigorous Patch Management: We constantly monitor platform components—from the OS to the control panel—and apply security patches the moment they’re released, closing the door on known exploits.
- Security Vetting: We build our platforms, like our Secure Web Hosting Bundles with Imunify360 and CloudLinux OS, using carefully chosen and hardened components to drastically reduce the risk of a compromised dependency. Imunify360 provides proactive defense against malware, while CloudLinux OS isolates tenants to prevent cross-contamination.
- Managed Firewall and Network Security: Our managed Juniper network devices enforce strict, least-privilege firewall rules. This means that even if a component were compromised, it can't "phone home" to an attacker's server, effectively containing the threat.
When you partner with ARPHost, you’re not just getting hosting; you're getting a team dedicated to securing every layer of your stack.
Ready to secure your applications from supply chain threats? Request a managed services quote today and let our experts fortify your defenses.
Protecting Your Data When Disaster Strikes: Beyond Simple Backups
When a security breach hits, everyone scrambles to stop the attack. But in that chaos, two silent killers are often ignored until it’s too late: data leakage and a flimsy disaster recovery (DR) plan. These aren't separate problems; they’re two sides of the same coin, representing a total failure to both protect your data and ensure business continuity.
Data leakage is the slow, uncontrolled bleed of sensitive information out of your network. Attackers might exploit unencrypted data streams or use stealthy techniques to siphon off records over weeks, disguising the theft as normal activity.
At the same time, you have the threat of a DR plan that’s nothing more than a document. Many businesses think having backups is enough, but modern ransomware has changed the rules. Attackers don't just encrypt your live data; they actively hunt down and obliterate your backups, leaving you with no path to recovery. An incident like that isn't just a setback—it's a potential extinction-level event.
Shifting from Reactive Backups to Proactive Recovery
A functional DR strategy must be built on one core assumption: your primary environment will be compromised. This is where proactive recovery comes in. It’s not about reacting after the fact; it’s about having a pre-built, tested, and entirely separate recovery path.
A modern, proactive DR plan isn't just a nice-to-have. It requires non-negotiable components:
- Isolation: Your backups must live in a separate, offsite location with completely different access credentials from your production environment.
- Immutability: This is your silver bullet against ransomware. Immutable backups are write-protected, meaning they can't be changed or deleted for a set period—not even by an administrator. This guarantees you’ll always have a clean, uncorrupted copy.
- Regular Testing: An untested backup isn't a plan; it's a prayer. Proactive recovery means you regularly run fire drills, simulating a full-blown disaster to test restore procedures and uncover gaps before a real crisis hits.
This shift in thinking treats disaster recovery not as a passive insurance policy but as an active defense against one of the most devastating vulnerabilities of cloud computing.
Having backups is not the same as having a recovery plan. A plan is a tested, automated, and isolated process that guarantees you can restore operations, while simple backups are just copies that can be easily wiped out alongside your primary data.
How ARPHost Fortifies Your Defenses
This is exactly the challenge ARPHost’s managed services were designed to solve. We take disaster recovery off the back burner and turn it into a managed, proactive strategy that delivers true business continuity.
With ARPHost’s Proxmox Backup as a Service, we give you offsite, encrypted storage that is completely walled off from your production servers. This is the foundation of a resilient infrastructure, and its real power comes from creating unchangeable restore points.
When you pair this with our fully managed IT services, we lift the entire weight of DR management from your team. Our experts handle everything—configuration, continuous monitoring, and regular testing of your backups—to ensure your recovery plan is always ready. We don't just sell you the tools; we manage the entire process, giving you the confidence that your business can survive the worst-case scenario.
Don't wait for a disaster to discover the holes in your safety net. Request a managed services quote today to build a proactive recovery plan with ARPHost.
Building a Proactive Defense with ARPHost
Knowing the vulnerabilities of cloud computing is the first step. The real shift happens when you move from a reactive, damage-control mindset to a proactive, fortified defense. This is where you stop just plugging holes and start building a foundation that's secure by design.
A proactive strategy doesn't just wait for an alert; it addresses each threat vector with a specific, powerful countermeasure, engineering vulnerabilities out of the picture from day one.
Mapping Vulnerabilities to ARPHost Solutions
For every cloud security challenge, there's a direct, practical solution within the ARPHost ecosystem. This one-to-one mapping is how we eliminate security gaps and replace uncertainty with genuine control.
- For Misconfigurations: Our Fully Managed IT Services act as your expert oversight. We implement hardened, least-privilege configurations from the very beginning, so your team never has to lose sleep over an accidentally exposed database or a forgotten firewall rule.
- For Hypervisor & Tenant Isolation Risks: Our Dedicated Proxmox Private Clouds eliminate this threat completely. By giving you dedicated bare-metal hardware, we take the "multi-tenant" problem off the table. Your resources are physically and logically yours, and yours alone.
- For API & Supply Chain Compromises: Our Secure Web Hosting Bundles come standard with Imunify360 and CloudLinux OS, creating a hardened software stack. We manage the network, control data flow, and apply patches rigorously to contain threats.
- For Data Leakage & Inadequate DR: Our Proxmox Backup as a Service leverages immutable, encrypted, offsite storage to make sure your recovery data is untouchable by ransomware. This turns disaster recovery from a hopeful plan into a tested, reliable business continuity engine.
This map shows exactly how a solid recovery plan acts as the bridge between a potential data breach and getting back to business as usual.
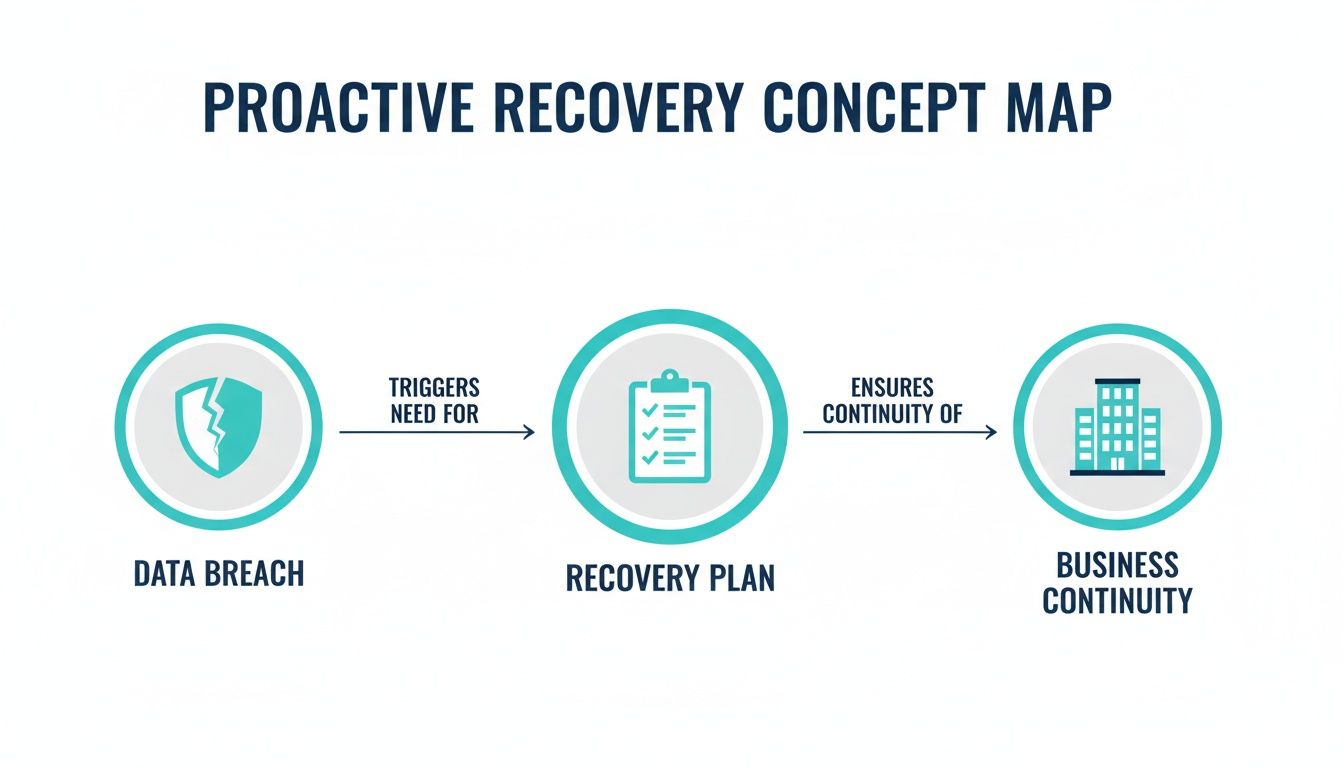
As you can see, a successful outcome is almost entirely dependent on having that robust plan in place before an incident occurs.
Why ARPHost Excels Here
When you work with ARPHost, you're choosing a proactive defense built on three pillars: expert human oversight, dedicated hardware, and integrated security tooling. It's the perfect foundation for implementing strong architectural principles like a Zero Trust Architecture design, which treats every request as a potential threat.
We don't just rent out servers; we deliver managed, secure, and resilient environments designed to withstand modern threats. Our offerings, from hyperconverged HA VPS plans built on KVM and CEPH storage to fully managed Virtual PBX phone systems, are engineered for security and performance.
With 24/7 expert support acting as a true extension of your team, we ensure your infrastructure is not only powerful but perpetually secure. It's about moving from defense as a reaction to defense as a core business advantage.
Take the first step toward a proactive defense. Explore our Dedicated Proxmox Private Cloud plans and build an environment free from shared risks.
Still Have Questions? Let's Clear a Few Things Up
Our team gets a lot of questions about cloud vulnerabilities and how to build a truly resilient infrastructure. Here are answers to a few of the most common ones we hear.
Is a Private Cloud Really More Secure Than a Major Public Cloud?
It’s true that public cloud providers pour massive amounts of money into security. But their entire model is built on sharing hardware, which introduces risks you simply can't engineer away—things like hypervisor vulnerabilities or a "noisy neighbor" hogging resources.
An ARPHost Dedicated Proxmox Private Cloud sidesteps these problems entirely. You get your own dedicated, single-tenant hardware. That means total resource isolation and complete control over the entire environment, which is a massive advantage when you're dealing with sensitive data or strict compliance rules.
How Technical Do I Need to Be to Run a Private Cloud with ARPHost?
That's the best part: you don't have to be. With our Fully Managed IT Services, our engineers handle everything. We're talking proactive monitoring, security hardening, patch management, backups—the works. We can even manage complex tasks like VMware to Proxmox 9 migrations.
You get all the security benefits of a dedicated private cloud without having to hire a team of sysadmins to babysit it. This frees you up to focus on what actually matters: running your business.
The greatest value of a managed private cloud is peace of mind. It transforms security from a complex, resource-draining task into a solved problem handled by dedicated experts, allowing your team to innovate instead of constantly patching vulnerabilities.
What's the Big Deal About Immutable Backups? Aren't All Backups the Same?
Not even close. A standard backup can be found and encrypted by ransomware right along with your live data. If an attacker gets in, your backups are just as vulnerable as everything else.
Immutable backups, like the ones we offer with our Proxmox Backup as a Service, are fundamentally different. They are write-protected, meaning they cannot be altered, encrypted, or deleted for a specific period. Even if your entire live environment is compromised, you have a guaranteed-clean copy of your data ready to restore. It makes ransomware almost powerless.
Here at ARPHost, we believe the only good defense is a proactive one. Our managed solutions are built from the ground up to shut down the most common cloud vulnerabilities before an attacker ever gets a chance to exploit them.
Ready to build an infrastructure that puts security first? Explore our Secure VPS Bundles and see how our team can help you get started.


