You’ve probably heard the term Security in Layers, or its more formal name, defense in depth. It’s a core cybersecurity strategy that boils down to a simple, powerful idea: use multiple, redundant defensive measures to protect your information.
If one layer fails, another is already in place to stop an attack. It’s all about making sure no single point of failure can compromise your entire system.
Understanding the Core of Layered Security

Think of your business infrastructure like a medieval fortress. A single outer wall is a decent start, but it's not going to stop a determined adversary for long. They could scale it, find a weak spot, or just smash right through it.
A truly secure fortress has multiple lines of defense. It has a wide moat, towering walls, guarded gatehouses, and vigilant watchtowers. And inside all of that, a final keep where the most valuable assets are stored.
That’s the essence of security in layers. Each defensive mechanism is designed to slow down, deter, and ultimately stop an attacker. Even if one layer is compromised—the moat is crossed or the outer wall is breached—the next layer is standing by. This approach turns your security from a fragile perimeter into a resilient, multi-faceted defense.
Why a Single Defense Is Not Enough
In the early days of the internet, many organizations relied on a strong perimeter firewall as their main defense. This "castle-and-moat" model is dangerously outdated today. Modern threats are far more sophisticated and can come from anywhere—including inside your network.
Relying on one control is like locking your front door but leaving all the windows wide open.
A single point of failure creates an unacceptable risk. A misconfigured firewall, a zero-day exploit, or a single stolen password could give an attacker the keys to the kingdom. A layered strategy mitigates this risk by working from the assumption that any individual control can, and eventually will, fail.
Defense in depth forces an attacker to defeat multiple, varied security controls to achieve their objective. This increases the cost and complexity of an attack, making your infrastructure a far less attractive target.
The Modern Approach to Layered Defense
The principle of layering security is more critical than ever. It forces attackers to navigate a complex web of technical and administrative controls, which dramatically increases the odds of them getting caught.
This philosophy is the foundation for modern security frameworks. If you want a pervasive approach rooted in assuming no implicit trust, you should learn how to implement Zero Trust security. The Zero Trust model perfectly complements a layered strategy by verifying every single request as if it originates from a hostile network.
By implementing overlapping security measures, you create a system that excels at:
- Deterrence: The sheer complexity of the defense discourages many would-be attackers.
- Detection: Each layer provides a new opportunity to identify and log suspicious activity.
- Delay: Breaching multiple layers slows attackers down, giving your team critical time to respond.
- Defense: If one layer fails, others are there to contain the threat and protect your most critical assets.
In this guide, we'll break down each of these layers, providing actionable examples and showing how ARPHost's managed services and secure hosting platforms can help you build this fortress.
Securing the Network Perimeter

Think of your network perimeter as the digital front door to your entire business. It's the first and most critical checkpoint in your defense, acting as a gatekeeper that inspects every single packet of data coming in or going out. A weak perimeter isn't just a vulnerability; it's an open invitation for trouble, which is why locking it down is the foundation of any real security in layers strategy.
Hardening this layer is about a deliberate, methodical approach to filtering traffic, spotting threats, and stopping attacks in their tracks. The need for this has never been more obvious. In a recent quarter alone, global cyber attacks skyrocketed by a staggering 75%, a wake-up call for anyone who thinks their current setup is "good enough." You can see the full breakdown in this detailed report.
Core Components of a Secure Perimeter
A truly secure perimeter isn't a single product but a combination of tools and policies working together. Each piece of the puzzle handles a different type of threat, creating overlapping fields of protection.
- Firewalls: This is the cornerstone. Modern next-generation firewalls (NGFWs) provide granular control over traffic based on ports, protocols, and applications. A properly configured firewall lives by a "deny by default" policy—if traffic isn't explicitly allowed, it's blocked.
- Intrusion Detection/Prevention Systems (IDS/IPS): While a firewall blocks known bad traffic, an IDS/IPS analyzes allowed traffic for suspicious patterns. An IDS alerts you to potential threats, while an IPS can automatically block them, like dropping malicious packets or blacklisting the source IP.
- DDoS Mitigation: Distributed Denial of Service (DDoS) attacks are pure brute force, designed to flood your network and knock your services offline. A key part of perimeter security is having specialized systems that can absorb and filter these massive traffic floods before they ever reach your critical servers.
Actionable Steps for Hardening the Perimeter
Putting these components to work requires careful planning. One of the most common mistakes is leaving unnecessary ports open. Every open port is another potential attack vector.
For a standard web server, a basic iptables ruleset should only permit traffic on essential ports while denying everything else.
Step 1: Set Default Policies to DROP
# Block all incoming, outgoing, and forwarded traffic by default
iptables -P INPUT DROP
iptables -P FORWARD DROP
iptables -P OUTPUT ACCEPT # Allow outbound traffic from the server
Step 2: Allow Established Connections
# Allow traffic for established connections to continue
iptables -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
Step 3: Open Essential Ports (HTTP, HTTPS, SSH)
# Allow web traffic
iptables -A INPUT -p tcp --dport 80 -j ACCEPT
iptables -A INPUT -p tcp --dport 443 -j ACCEPT
# Allow SSH from a trusted IP only (replace with your IP)
iptables -A INPUT -p tcp -s YOUR_TRUSTED_IP --dport 22 -j ACCEPT
This simple "principle of least privilege" drastically shrinks your attack surface.
At ARPHost, our managed network services are built on enterprise-grade Juniper hardware. Our team helps you implement and manage advanced firewall rulesets, ensuring your perimeter is locked down tight without disrupting legitimate business operations.
Scaling Perimeter Security with ARPHost
Manually managing firewalls, watching for intrusions, and fending off DDoS attacks is a 24/7 job that requires deep expertise. This is where a managed approach makes all the difference.
ARPHost builds perimeter security right into our services. Our fully managed IT services include proactive firewall management and network monitoring, so your rules stay optimized and threats get spotted fast. For businesses in high-risk environments, our DDoS-protected dedicated servers are engineered to withstand massive attacks and keep you online.
By handing off your perimeter defense to our team, you can focus on what you do best, knowing your first line of defense is solid and actively managed by security professionals.
Hardening Servers and Endpoints
So, what happens if a determined attacker punches through your network defenses? Their next stop is the heart of your operation: the servers and endpoints. This is the host layer, where your data lives and your applications run. Locking these machines down isn't just a good idea; it's a non-negotiable part of any real security in layers strategy. You have to turn each machine from a potential weak link into a hardened fortress.
"Hardening" a server is all about shrinking its attack surface. You systematically remove any software that isn't essential, shut down unused network ports, and enforce permissions with an iron fist. The goal is to apply the principle of least privilege everywhere, making sure the machine does its job and absolutely nothing more.
Unfortunately, this is where many businesses drop the ball. A staggering 35% of small businesses now report having insufficient cyber resilience—a sevenfold jump since 2022. This highlights the critical need for robust, automated host-level security.
Foundational Server Hardening Techniques
A secure server is a lean server. The first, and most important, step is to take a full inventory of every service and piece of software running on it. If it’s not mission-critical for that server's role, it needs to go.
For example, on a Linux VPS, you can get a quick look at all open listening ports with a simple command:
# View all listening TCP and UDP ports
ss -tuln
This shows you exactly what "doors" are open to the network. If you spot a service you don't need—like an old FTP daemon running on a dedicated web server—shut it down.
# Example for a systemd-based system
systemctl stop vsftpd
systemctl disable vsftpd
That single action instantly removes a target from an attacker's list. Next is proactive patch management. A disciplined, regular patching schedule is your best defense against known exploits.
For a complete walkthrough of these techniques and other critical host-level security measures, check out our guide on how to secure a web server.
Essential Host Security Controls Checklist
Implementing these controls manually across multiple servers is tough. Here’s a quick look at how a managed solution streamlines the process.
| Security Control | Manual Implementation (Unmanaged) | ARPHost Managed Solution |
|---|---|---|
| OS Hardening | Manually disable services, remove packages, configure kernel settings. | Pre-hardened OS images deployed by default. |
| Patch Management | Requires manual tracking and execution of apt update, yum update, etc. | Automated, scheduled patching with regression testing. |
| Intrusion Detection | Install & configure tools like fail2ban or ossec yourself. | Integrated Intrusion Detection & Prevention System (Imunify360). |
| Malware Scanning | Set up cron jobs for manual scans with tools like ClamAV. | Proactive, real-time malware scanning and automatic cleanup. |
| Account Isolation | Requires complex user/group permissions and chroot jails. | Built-in account isolation with CloudLinux OS cages. |
| Web App Firewall (WAF) | Manually install and configure ModSecurity with complex rule sets. | Advanced WAF with proactive defense rules, managed for you. |
As you can see, a managed approach offloads the repetitive, error-prone work, letting security experts handle the heavy lifting while you focus on your business.
Automating Host Security With ARPHost
Manually hardening every single server is not just time-consuming; it's a recipe for human error, especially as you scale. This is where ARPHost's managed solutions really shine, automating these critical security tasks around the clock.
Our Secure web hosting bundles are built from the ground up with host security in mind. We integrate industry-leading tools to create a hardened environment right out of the box:
- CloudLinux OS: This isn't your standard operating system. It creates a virtualized "cage" for each user on a server. This isolation is a core principle of layered security—if one account is ever compromised, the breach is contained and cannot spread to others on the same machine.
- Imunify360: Think of this as an all-in-one security guard for your server. It bundles an advanced firewall, proactive malware scanning, intrusion detection, and automated defense against brute-force attacks. It effectively handles many of the essential hardening steps we've talked about, all on its own.
By choosing a secure managed VPS from ARPHost, you're not just renting a server; you're getting an entire security ecosystem. Our platforms come pre-hardened and are proactively managed, delivering automated protection that works 24/7 to keep your hosts secure.
Whether you're running a simple website on our affordable VPS hosting (from $5.99/month) or handling complex applications on a bare metal server, our managed services ensure the host layer is a bastion of defense, not a point of failure.
Protecting Applications and Data

We've made it to the very heart of the fortress. Deep inside all the other defenses lie your most valuable assets: the applications that run your business and the data they churn through. No matter how many walls an attacker scales, this is their ultimate prize.
Any worthwhile security in layers strategy saves its strongest controls for these crown jewels. The focus shifts from protecting the infrastructure around your assets to protecting the assets themselves—shielding your code from exploits and guaranteeing your data remains confidential, intact, and available.
Shielding Applications with a WAF
Even if your server is locked down tight, the application itself can be the weakest link. Common vulnerabilities like SQL injection and Cross-Site Scripting (XSS) are a constant threat. Secure coding is the goal, but it demands relentless perfection.
This is where a Web Application Firewall (WAF) becomes an absolute game-changer. A WAF is like a specialized bodyguard for your web app, inspecting all incoming traffic for patterns that match known attack techniques. It blocks malicious requests before they ever get a chance to touch your application's code.
For instance, a WAF can spot and instantly shut down a request stuffed with classic SQL injection code like ' OR 1=1; --. It provides a crucial safety net, protecting your applications even if a sneaky code vulnerability slips through the cracks.
Why ARPHost Excels Here
Manually configuring and fine-tuning WAF rules is a full-time job. ARPHost's Secure VPS hosting bundles take this off your plate by integrating Imunify360. This security suite includes a managed WAF with rules that are constantly updated, giving you proactive protection against the latest threats for platforms like WordPress, Joomla, and Magento.
Implementing Robust Data Protection
Protecting data isn't just about locking the door. It's about safeguarding it through its entire lifecycle with a strategy that weaves together encryption, smart access controls, and bulletproof backup plans.
Key data protection controls you need to have in place include:
- Encryption in Transit: Using TLS/SSL to scramble data as it travels between a user's browser and your server.
- Encryption at Rest: Encrypting all the data sitting on your server's hard drives. If someone physically stole the hardware, the data would be unreadable without the decryption keys.
- Role-Based Access Control (RBAC): Applying the principle of least privilege directly to your databases. This means creating user roles with just enough permission to do their job—and nothing more. For example, a "read-only" user for reporting can't modify or delete data.
Finally, a critical part of the data lifecycle is making sure sensitive information is gone for good when you don't need it anymore. For a deep dive into best practices, check out this guide to secure data destruction.
The Ultimate Safety Net: Secure Backups
No security strategy is complete without a solid recovery plan. Hardware fails, data gets corrupted, and ransomware can bring your entire operation to a screeching halt. Your final, and arguably most important, layer of defense is automated, secure backups.
The key is to keep these backups completely isolated from your main production environment. That way, they won't get caught in the crossfire during an attack.
ARPHost's managed services and Dedicated Proxmox private clouds are built around this core principle. We provide automated backup solutions that create secure, off-site copies of your critical data, ensuring you can restore everything and get back to business quickly. This turns a potential catastrophe into a manageable hiccup.
For the highest level of protection available, you can explore options like immutable backup solutions. These make it physically impossible for ransomware to encrypt or delete your recovery points, giving you an unbreakable last line of defense.
Strengthening the Human Layer
You can build the most secure digital fortress imaginable, but it only takes one person clicking one bad link for the whole thing to come crashing down. Your technology stack can be perfectly hardened, but attackers know the human layer is often the weakest point of entry. Strengthening this layer isn't about pointing fingers; it's about empowering your team with the right policies, training, and tools.
A solid security in layers model accepts a simple truth: technology alone is not a silver bullet. Your team has to be an active, educated part of your defense. This means building a security-first culture where every single person understands their role in protecting the company’s digital assets.
Building a Foundation of Strong Security Policies
Clear, common-sense policies are the bedrock of your human defenses. These aren't just dusty documents for auditors; they are practical guides that set clear expectations for how everyone should behave online and with company data.
A few must-have policies include:
- Acceptable Use Policy (AUP): Lays out the ground rules for using company equipment, networks, and servers.
- Password Policy: Mandates strong, unique passwords, sets rotation schedules, and bans recycling old ones.
- Data Handling Policy: Spells out how to classify sensitive information and exactly how it should be stored, sent, and eventually destroyed.
These policies eliminate guesswork and create a consistent security posture. The global average for national cybersecurity has climbed to 65.7 out of 100, a 27% jump in recent years, showing a serious international shift toward implementing security across every level of infrastructure—including the human and policy layers. You can dig into the specifics of these global cybersecurity improvements to see how nations are adapting.
Implementing Least Privilege and MFA
Two controls are absolutely non-negotiable for locking down the human layer: the Principle of Least Privilege and Multi-Factor Authentication (MFA).
The Principle of Least Privilege is simple: people should only have access to the specific data and systems they absolutely need to do their jobs. Nothing more. Someone in marketing, for instance, has no business with admin access to production databases. This single concept dramatically shrinks the potential damage if an account is ever compromised.
Multi-Factor Authentication (MFA) is the single most effective control you can implement to protect user accounts. It forces users to prove their identity with two or more factors, making a stolen password almost useless to an attacker.
MFA isn't optional. It should be mandatory on every critical system, including:
- Server and Control Panel Access: For every administrative login to your VPS hosting or Dedicated Proxmox Private Clouds.
- Email and Collaboration Tools: Protecting your organization's primary communication channels is a must.
- Virtual PBX Phone Systems: Securing access to your business phone lines and call data.
The ARPHost Managed Approach to the Human Layer
Developing, implementing, and enforcing these rules takes a lot of work and constant vigilance. This is where ARPHost's fully managed IT services come in. We partner with you to lock down every access point.
We can configure role-based access controls on your managed servers, enforce MFA policies across the board, and manage user permissions on systems like your Virtual PBX phone system. This partnership ensures that security best practices aren't just written down in a document—they're actively implemented, monitored, and enforced across your entire infrastructure.
Ready to fortify your team against modern threats? Request a quote for our fully managed IT services and let our experts help you build a human security layer that’s just as strong as your tech.
How ARPHost Delivers Your Defense in Depth
Talking about a security in layers strategy is one thing; actually building it is another. It's a complex, ongoing effort that requires real expertise across multiple domains. This is where we connect the dots, showing you exactly how ARPHost’s managed solutions give you the tools and the expert oversight to build your digital fortress, layer by layer.
We don't just sell you the bricks and mortar. We're here to translate security theory into tangible business outcomes—peace of mind, reduced operational risk, and a security partner you can actually call. We help you construct and maintain the entire defensive structure, making sure every layer works in harmony for maximum protection.
A Unified Security Ecosystem
At ARPHost, we map our services directly to the defense-in-depth model. This creates a unified security ecosystem that protects you from the network edge all the way down to your end-users.
Perimeter Security: Our managed network services are your first line of defense, built on enterprise-grade Juniper hardware. We configure strict firewall rules and deploy DDoS mitigation to filter out malicious traffic long before it has a chance to reach your servers.
Host & Application Security: Our Secure web hosting bundles are designed to harden the server and application layers right out of the box. They feature CloudLinux OS for total account isolation and Imunify360 for proactive threat management, which includes an advanced Web Application Firewall (WAF). Your servers become hardened assets from day one.
Data Security: Whether you're on bare metal servers or one of our Dedicated Proxmox Private Clouds, we provide the foundation for robust data protection. Our services include automated, isolated backups and give you the power to implement strong encryption and access controls, safeguarding your most critical information.
Fortifying the Human Layer
The human element is a critical—and often overlooked—security layer. After all, the most sophisticated firewall in the world can't stop someone from clicking a bad link. This diagram shows the core components of a strong human defense.
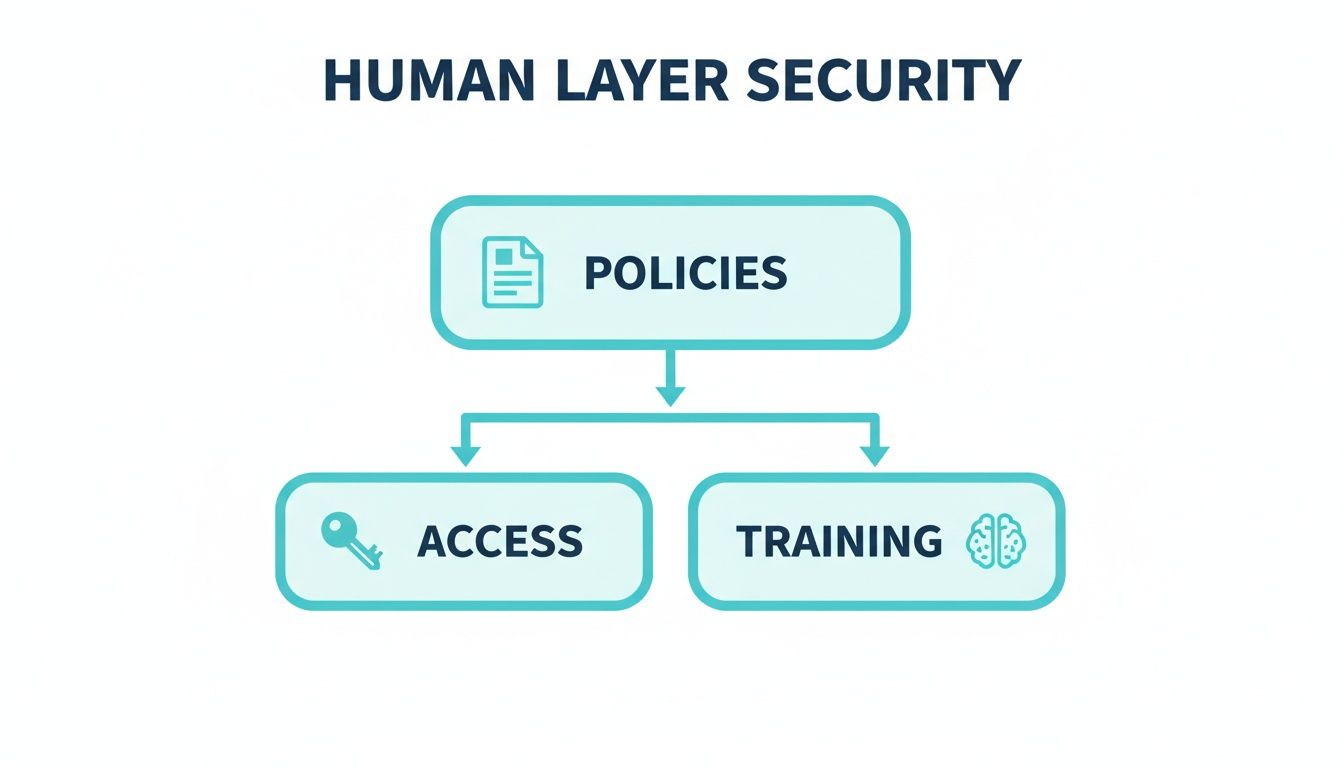
As you can see, effective security starts with clear policies, is enforced through strict access controls, and is maintained with ongoing user training. ARPHost's fully managed IT services help you implement and enforce these principles across your infrastructure, from managing user permissions on servers to securing your Virtual PBX phone systems.
When you partner with ARPHost, you get a dedicated team of experts focused on building and managing your layered defense. This lets you get back to your core business, confident that a complete, professionally managed security strategy is protecting your assets around the clock.
Ready to build your fortress? Explore our Secure VPS Bundles at arphost.com/vps-web-hosting-security-bundles/ to get started with an all-in-one hardened solution.
Common Questions About Layered Security
When you start digging into a defense-in-depth strategy, a few practical questions always come up. Here are some straightforward answers to the things we hear most often from businesses looking to get serious about their security.
Is A Firewall Enough to Protect My Server?
Nope. A firewall is a critical first line of defense—think of it as the strong front door to your house—but it's never enough on its own. Attackers have countless ways to get past that front door, from exploiting a tiny flaw in an application to simply using stolen keys (compromised credentials).
A real security in layers strategy assumes the perimeter will eventually be breached. It adds locks to the internal doors by protecting the server itself with anti-malware and timely patch management, securing the web application with a Web Application Firewall (WAF), and encrypting your sensitive data so it's useless even if stolen.
ARPHost's Secure VPS bundles build these layers for you right out of the box. You get a firewall, WAF, malware scanner, and an intrusion detection system like Imunify360 all working in concert. It's a massive upgrade from relying on a single point of failure.
How Much Technical Knowledge Do I Need?
If you're going it alone, a lot. Manually configuring every security layer is a full-time job for a seasoned professional. You’d need deep expertise in networking, server administration, and application security just to get started—hardening the operating system, fine-tuning firewall rules, managing a WAF, and constantly monitoring logs for threats.
This is exactly why managed services exist. With a provider like ARPHost, you're essentially hiring our entire team of experts. Our fully managed IT services and secure hosting plans are designed to handle all of that complexity for you, implementing best practices so you can focus on running your business, not fighting off attackers.
Can I Apply A Layered Security Model to A Private Cloud?
Absolutely. In fact, a private cloud is one of the best environments for building a powerful layered security model. It gives you the granular control you need to construct a truly segmented and resilient defense from the ground up.
With ARPHost's Dedicated Proxmox Private Clouds, you have full root access over your own dedicated hardware. This lets you architect distinct layers of security that just aren't possible in a shared environment:
- Network Layer: You can deploy dedicated virtual firewalls at the edge to inspect and control every packet coming in or out.
- Virtualization Layer: Create strict network segmentation between your virtual machines. If one VM is compromised, the blast radius is contained, preventing the threat from spreading sideways.
- Host Layer: Apply unique security policies, access rules, and hardening configurations to each individual VM based on its role.
This kind of structure offers unmatched isolation and protection for your most critical applications, making it the perfect foundation for a serious defense-in-depth strategy.
Ready to build a resilient, multi-layered defense without the management headache? The expert team at ARPHost is here to help design and implement a security strategy that fits your exact needs.
Explore our Dedicated Proxmox Private Cloud plans and gain full control over your secure environment.


